With the introduction of the A12 chip, Apple strengthened the security around generating nonces, saving blobs, and restoring in general. The basic process remains the same, but due to a feature called nonce-entanglement (yes, really), there are a few extra hoops we need to jump through to save valid blobs. This tutorial will show you how to do so.
First of all, if you have a device older than A12 era (before iPhone XS, XR, etc.), you do not need to follow this guide. Your process is simpler, and you should refer to our main guide for saving blobs.
Second, if you have a device A12 and newer (iPhone XS, XR, and everything newer released by Apple into the future), you MUST follow this guide. If you don’t, the blobs you save will be invalid.
This is a supplementary guide to be used in addition to our main guide. A12+ users must start with this guide, complete the steps, and then move to the main guide to finish the process.
You will only need to complete this guide once per A12+ device that you own. Once you have gathered the pieces of information about your device which this guide will give you, you will save them for future reference. You will then be able to save blobs in future using the main guide only, by entering those pieces of information, without having to repeat the process described in this guide.
I cover Mac, Linux, and Windows here, but can provide support for Mac only. Mac and Linux use the official, and identical, tool releases, so I recommend them where possible.
Lastly, you will need a jailbreak on your A12+ device to complete this guide. If you don’t, the values you discover will be useless. Once you have found the necessary values using this guide you do not need to keep a jailbreak to save future blobs. You can use the values discovered in this guide, which you will save for future reference, to save valid blobs going forward, even if your device is not jailbroken.
But to repeat, you must have a jailbreak on your A12+ device at least once, at the time that you follow this guide, in order to gather the correct information. Let’s get started…
Prerequisites…
Linux
Install libimobiledevice, libirecovery, and their dependencies using a package manager of your choice, such as apt.
Windows
Well known tweak developer Tateu has compiled versions of the required tools for Windows, which you can download here. I have not tested these and cannot provide Windows support. You will also need iTunes installed on your computer.
Mac
Open Terminal and run the following commands:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
This installs Homebrew on your Mac.
brew update
This updates Homebrew to the newest contents.
brew install --HEAD usbmuxd
brew install --HEAD libimobiledevice
brew install libirecovery
These install the components required to interact with, and extract the info we need from, our device.
Errors with installing the tools needed for this guide, and/or installing Homebrew (Mac only) are beyond the scope of this guide and will be down to the user to troubleshoot. This guide assumes that installing Homebrew (Mac only), iTunes (Windows only), and the tools/binaries we need (all OSes), has been successfully completed before continuing.
Preparing the device
We now need to set a known generator on our device, which requires a jailbreak. A12 and above devices will create a different Apnonce for every different generator that is set, and the blobs we save will need that specific Apnonce in order to be valid. Therefore, we must know what generator we used to create our Apnonce, or we will not be able to use the blobs to restore at a later date.
So, we will set a generator on our device, make a note of it, find the unique Apnonce it produces, make a note of that, and then use these pair of values, and only these pair of values, to save our future blobs, and to restore our device with those blobs in future.
How to set a known generator varies depending on what jailbreak you are using:
unc0ver/Odyssey/Chimera
You can set a generator via the jailbreak app itself. Open the jailbreak app, open its settings page, and enter a generator. You may need to press Apply or similar and/or respring your device to finish setting the generator.
Others
The process on older or not-mentioned jailbreaks may vary, and you will need research how to do it yourself. In general, they will have a method for setting a generator using either a standalone tweak, a side-loaded “generator setter” app, or via the jailbreak app itself.
checkra1n (A11 and below only)
Add the following repo to your device:
https://halo-michael.github.io/repo
And install the package called Generator Auto Setter. Once installed, go to your tweaks in the Settings app, find Generator Auto Setter, enter a generator of your choice, and select Set.
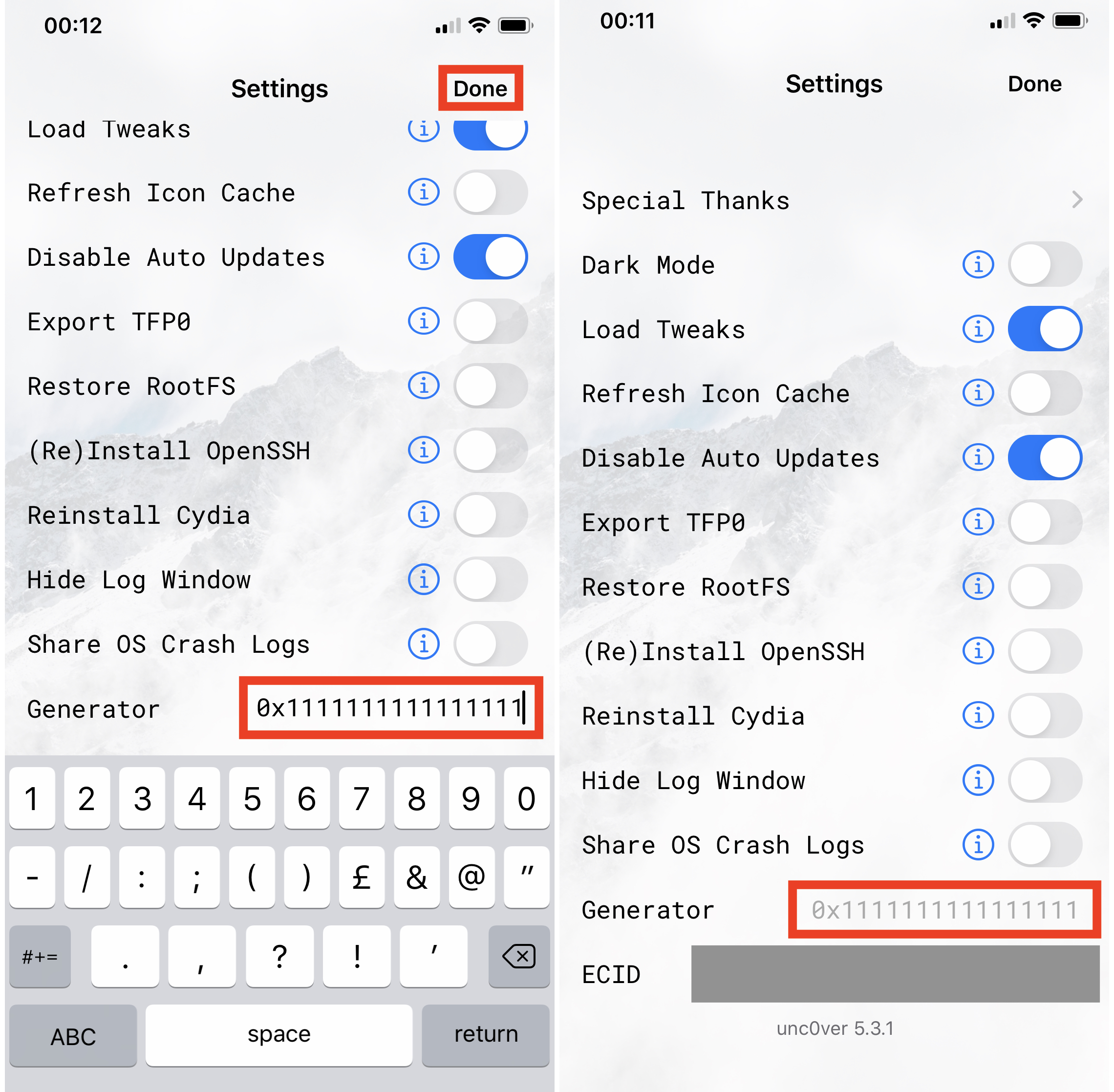
Please note, it does not matter what generator you set. What matters is that you must know which generator you set, before discovering its matching Apnonce. They make a pair, and changing the generator will change the Apnonce. We need to know what generator created the Apnonce we will discover in the next steps. Many generator setters use a default value. For example, unc0ver and Generator Auto Setter both use 0x1111111111111111 by default. Your generator setter may use a different value. You can leave the generator set as the default value (recommended), or you can change it. It does not matter as long as you know what you have set it to, and note it down.
Once you have successfully set the generator on your jailbroken device to a known value, such as 0x1111111111111111, and have your device plugged into your computer, we can proceed.
Remember: know what your generator value is, and note it somewhere safe (like a text document) for the future! If you no longer know what generator you used to create the Apnonce which you use to save your blobs, your blobs will become useless for restoring.
Finding the values we need
So you’ve installed the tools you need on your computer, set a known generator on your A12+ device, and plugged your device into your computer. Make sure you have “trusted” your computer from your device so they can interact. This only needs to be done once per device for a given computer, and is done through iTunes, Finder, or Apple Configurator, and on your device’s screen by entering your passcode.
One last note, do not reboot or unjailbreak your device between setting the generator in the previous step and completing these next steps. When you reboot your device, the generator is randomised by the OS, which would make the next steps useless. We must have a known generator in place when we complete the following steps, so set the generator as described above and proceed immediately with the rest of this guide.
Now open a Terminal window. On Windows you will also need to navigate to where the binaries you downloaded are stored before running the following commands. If any of these commands fail on Mac or Linux, try running them with the word sudo in front of them. Enter the following:
irecovery
This command should print a list of options when run. If you see a message saying “Command not found” or anything similar, do not proceed. Return to the Prerequisites… section and fix your installation of libirecovery. If you don’t, your device will get stuck in Recovery Mode later on.
Now enter:
ideviceinfo
You should see a long list of information about your connected device. You will need to copy down the values for HardwareModel (this is your board config), ProductType (this is your device model), and UniqueDeviceID (this is the UDID which we need for the next step).
Note these values down somewhere safe, like in the text document where you saved your generator earlier. You will need them every time you save blobs later.
Now enter:
ideviceenterrecovery UDID
Replace UDID with the UniqueDeviceID (a long string of numbers and letters) which you just noted down in the previous step. Your device will now reboot into recovery mode, and you should see the accompanying graphic on its screen.
Now enter:
irecovery -q
You should see another list of values for your device. You will need to copy down the values for ECID (this is your device’s ECID, needed every time you save blobs), and NONC (this is the vitally important Apnonce we have been hearing so much about, and is uniquely paired to the generator we set earlier).
Note these values down somewhere safe, like in the text document where you saved your generator, HardwareModel, and ProductType earlier. You will need them every time you save blobs later.
Finally, enter:
irecovery -n
This will reboot your device back out of recovery mode. Do not reboot the device with the physical buttons, as it will always return to recovery mode. Use this command instead.
Finishing up
So your device is safely rebooted back into normal mode and you have a list of values for your device, which you will safely keep forever. The list contains:
- Your board config (noted down earlier as HardwareModel)
- Your exact device model (noted down earlier as ProductType)
- Your ECID (an alphanumeric string likely beginning with 0x…)
- Your known generator (set by you at the start, for example 0x1111111111111111)
- Your Apnonce (a long alphanumeric string, which is valid only for the generator you set above)
You are now ready to save .shsh2 blobs for your A12+ device. In future you will not need to repeat this guide to save blobs for this device. You do not even have to keep a jailbreak on it in order to save blobs, though you will need one to use them to restore in future. To save blobs going forward, simply enter your saved list of values into your blob saver when requested. In fact, let’s do that now…
Now (and on any future occasions when you want to save blobs for your A12+ device) proceed directly to our general guide for saving blobs with TSS Saver. Skip straight to Step 5 in that guide, and continue through, entering the values we collected here when prompted. Good luck!




