Sam Boyd
Updated on: December 28, 2023
Short on time? Here’s how to remove ByteFence Secure Browsing:
- 1. Remove Malicious Web Extensions and Reset Browser Defaults — Navigate into your default web browser’s extension/plug-in settings, and remove any malicious extensions you’ve accidentally installed. Then, restore your homepage and search engine to the original options in your web browser’s settings menu.
- 2. Scan Your Device — Complete a full disk scan using a premium antivirus — Norton is my top choice.
- 3. Remove spyware and other viruses — After the scan is complete, let the antivirus remove all instances of the browser hijacker and any other viruses it finds.
- 4. Keep Yourself Protected — Avoid falling victim to malware again by choosing a premium internet security suite. My favorite, Norton, will protect you online with its advanced malware scanner and useful extras like anti-phishing and an unlimited VPN. All plans come with a 60-day money-back guarantee.
ByteFence Secure Browsing is a browser hijacker/spyware tool that steals your private information (such as IP address) and monitors your online activity. ByteFence Secure Browsing installs an extension to your web browser that displays annoying pop-ups and redirects your online searches through ByteFence’s non-secure search engine.
Note: Secured Search is a new variant of the ByteFence Secure Browsing hijacker. If your browser has been infected with Secured Search, you can follow all of the advice in this article to clean up your browser and keep yourself safe from future spyware, browser hijackers, and other malware files.
If your default search engine has changed to ByteFence Secure Browsing Search, it indicates that this spyware has infected your computer. You will need to remove the ByteFence Secure Browsing browser extension, restore your web browser’s homepage and search engine back to its original settings, and then scan your computer with a comprehensive antivirus scanner (like Norton).
Spyware files like ByteFence Secure Browsing aren’t as dangerous as malware files like ransomware, trojans, crytpojackers, or rootkits. But if your device is infected with spyware, there’s a good chance that your system is also infected with dangerous malware files.
Removing Bytefence Secure Browsing (and keeping your device secure afterward) is easy if you follow the right steps. The good news is that Norton, our favorite antivirus of 2024, offers affordable plans starting at just $54.99 / year*, and you can try it with a 60-day money-back guarantee.
60-Days Risk-Free — Try Norton Now
Preliminary Step: Remove the Malicious Extensions in Your Web Browser and Reset Your Search Engine to Its Default Settings
Since ByteFence Secure Browsing utilizes a web extension, you can easily uninstall it.
Uninstalling Web Extensions in Chromium-Based Browsers
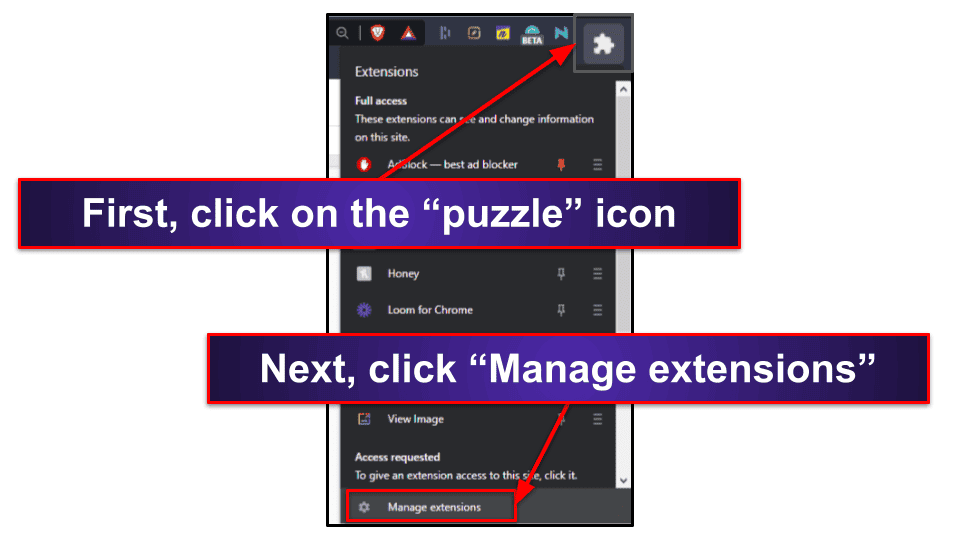
In Chromium-based browsers, such as Google Chrome, Microsoft Edge, and Brave, click on the “puzzle” icon in the top right corner of your screen, and then click, “Manage extensions.”
Next, navigate through your extension list until you see “ByteFence Secure Browsing” and click “Remove”.
A pop-up will appear asking you to confirm your choice. Click “Remove” on the pop-up, and your Chromium-based browser will remove the ByteFence Secure Browsing add-on.
You can then proceed to resetting your home page’s default settings.
Uninstalling Web Extensions in Firefox
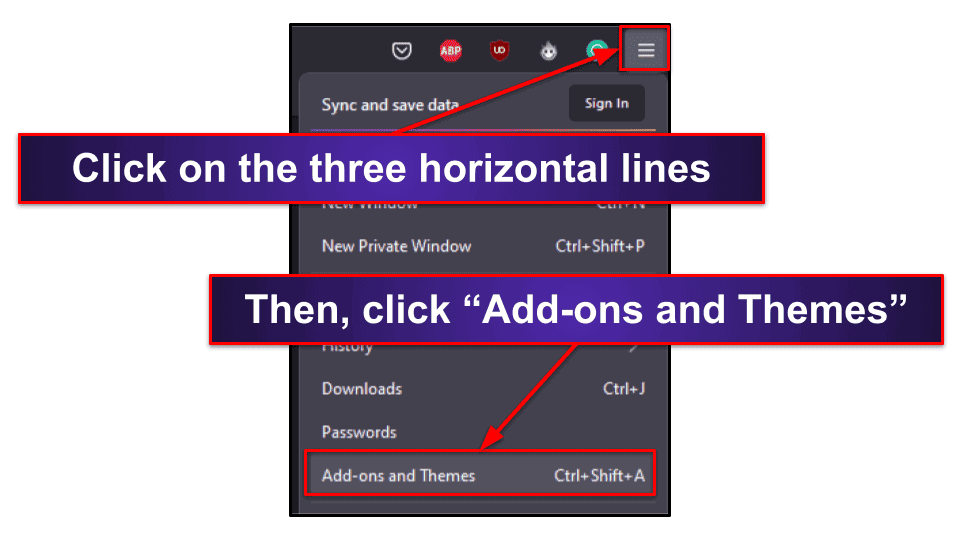
Removing add-ons from Firefox users is very similar to removing them from a Chromium browser. Click on the three horizontal lines in the top right of your browser, and click “Add-ons and Themes.”
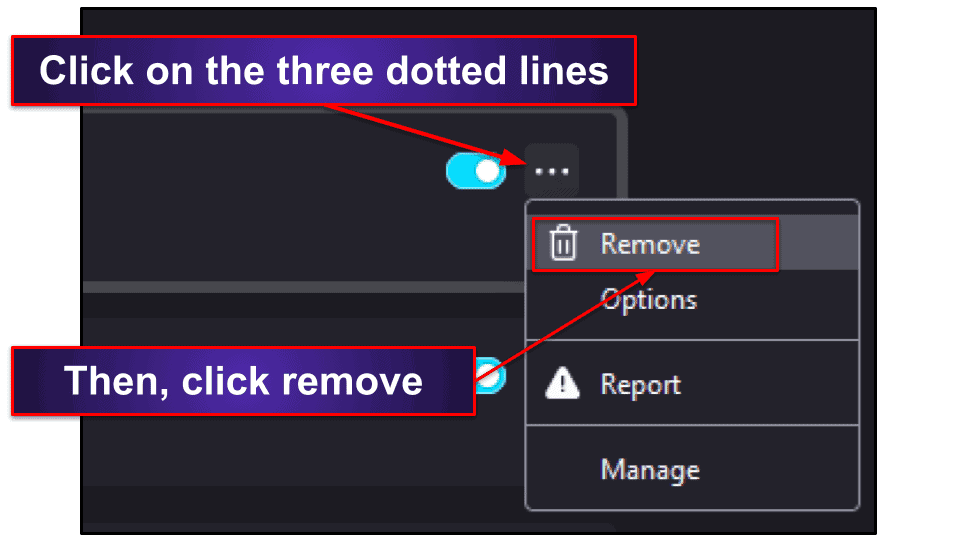
Find ByteFence Secure Browsing under the “Enabled” extensions list, click the three horizontal dots next to it, and click “Remove.”
However, on both Chromium and Firefox, you’ll also have to reset your web browser’s homepage and search engine to their default settings.
Resetting Your Web Browser’s Default Search Engine and Home Page.
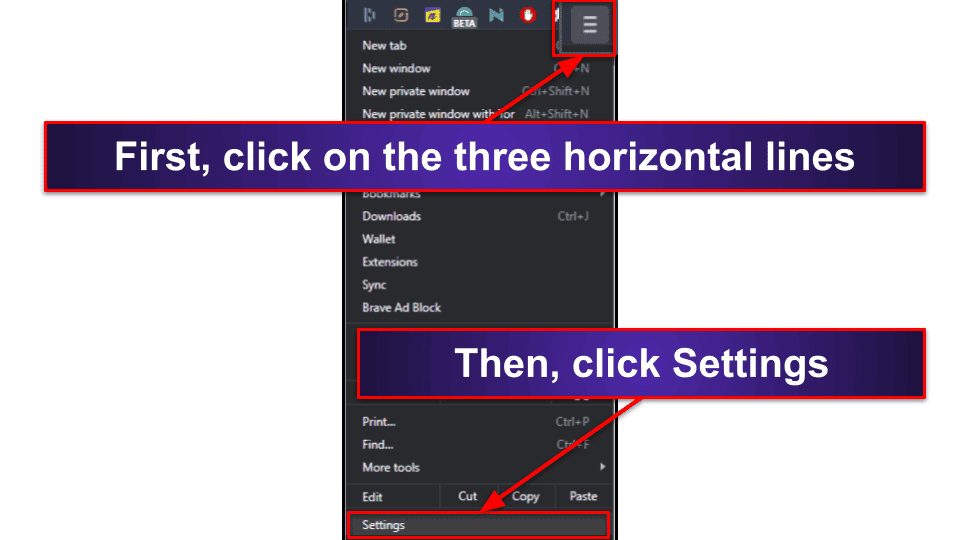
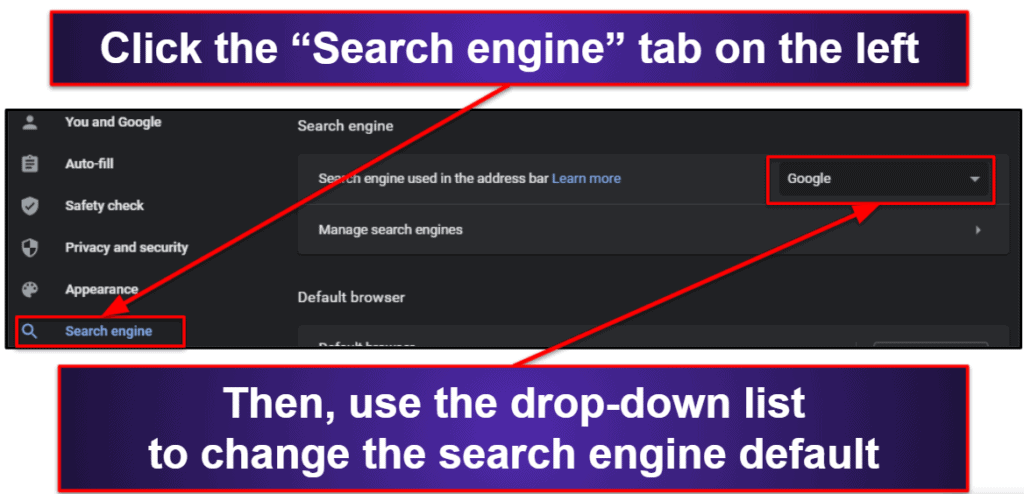
In both Chromium and Firefox, click the three horizontal lines (or dots) in the top right of your screen, and then click, “Settings”.
Then, click the “Search engine” tab on the left side of your screen (“Search” in Firefox). You will find a drop-down list here where you can change your default search engine.
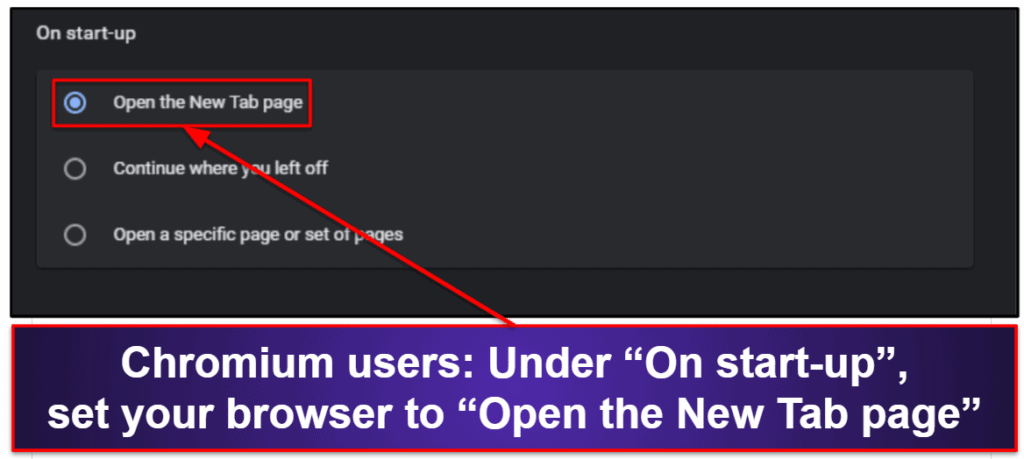
On Chromium-based browsers, you can also change what your browser does on start-up in the “Search engine” tab. Your best bet is to have start-up options set to “Open the New Tab page.”
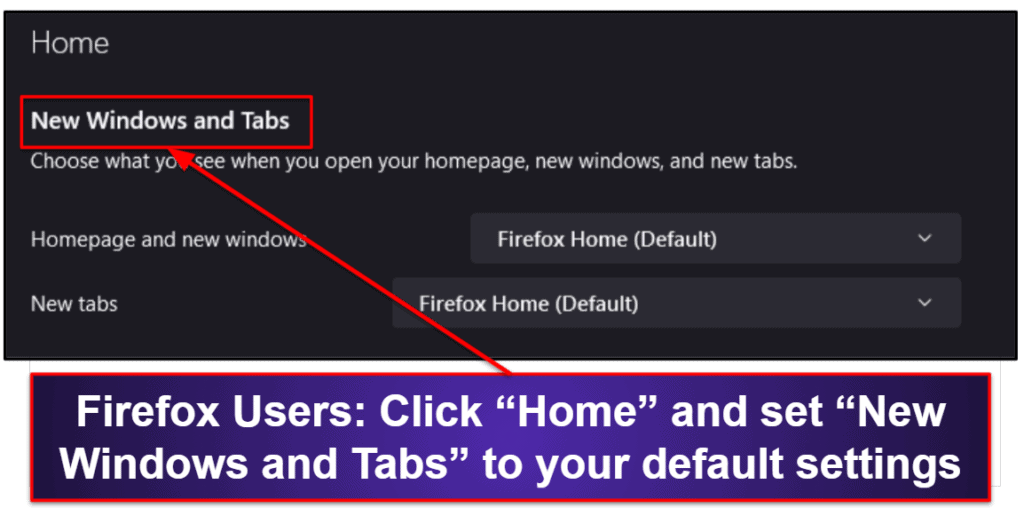
Firefox users will have to click on the “Home” tab on the left side of the screen to find the same start-up options.
Once you’ve done this, all traces of ByteFence Secure Browsing will be gone from your web browser.
Your next step is to scan your PC with a comprehensive antivirus like Norton to make sure all traces of malicious files are gone from your system.
Step 1. Run a Full System Scan With Your Antivirus
If you think that you possibly have ByteFence Secure Browsing on your computer, first you need to remove all USB storage devices from your computer. Otherwise, you risk malware copying itself onto those devices — if you’re worried that the malware replicated itself on your other devices, you can run a full scan of them as well with your antivirus.
Once all USB devices are removed, run a full disk scan with your antivirus — it will scan all of the files on your computer and place any suspected malware it finds into quarantine. The scan may last 4-5 hours, so I recommend scheduling the scan at a time when you don’t need to use your computer.
It’s crucial that you let the full system scan run until it’s 100% complete. Malware can make copies of itself, and if you cancel the scan early, there’s a good chance your antivirus won’t detect all of the malware.
Step 2. Delete Any Infected Files
Your next step is to review and delete all of the files that your antivirus has placed in the quarantine vault. If your antivirus detected additional infected files other than ByteFence Secure Browsing, advanced users can check for false positives — but make sure a file is 100% safe before you decide to keep it.
Once you’ve deleted every piece of malware in the quarantine file list, it’s easy to think that the malware threat is over. However, there may still be more malware running in Windows memory. To stop these malware threats from running, you need to restart your PC. Once your PC has restarted, run a second full disk scan to ensure no malware has replicated itself (the second scan should be quicker than the initial one because most antivirus scanners, like Norton, can recognize files that have already been scanned).
When the second full disk scan has finished, check your quarantine vault to see if your antivirus detected any malware. If there are malware files displayed on your quarantine list, you need to restart your PC again and repeat these steps until all of the malware has been removed from your computer.
While your computer is no longer infected with malware, you need to take the necessary steps to ensure you don’t get infected again.
Step 3. Keep Your Device Protected From Other Unwanted Programs
There are new threats appearing on the internet every day in 2024. However, it’s easy to ensure you’re protected from these growing threats by following the right steps.
Keep Your Software, OS, and Drivers Up-To-Date
Keeping your software, operating system, and drivers up to date is an important step often overlooked by users. Cybercriminals can take advantage of obsolete software through an exploit attack, which uses outdated software to create a backdoor into your system (and may cause irreparable damage to your computer). However, developers help keep your computer safe by issuing updates that fix any security flaws in outdated software.
Also, you can use other easy and convenient tools to ensure your system is updated. For example, an antivirus like Avira scans your software and drivers for any vulnerabilities, automatically updating any outdated software, drivers, and programs for you.
Another way to keep your computer updated is to enable the auto-update option on your applications — it will perform an update when you open the app.
It’s also important to access Windows updates to check for updates and schedule them to run at a specific time. Windows has many optional updates, including for new features and some non-essential security fixes that cybercriminals may still target.
Don’t Download Suspicious Files
You should never download a file from an untrusted website or click on an email attachment from an unknown sender — they are the easiest ways for viruses to spread to your computer.
When receiving an email, always check if the sender is someone you recognize. If it is, but you weren’t expecting an attachment from them, you should contact them outside of email and confirm they intended to send you an attachment. If they never sent you an attachment, their account may have been compromised and you should delete the email.
You should also watch out for emails that disguise themselves as trusted businesses. These emails trick you into a false sense of security because they contain the same branding as the trusted business. However, often the email will contain malicious links and downloads. If you’re not sure about an email you received from a business, contact them to get confirmation.
The best way to stay safe from downloading a suspicious file or clicking on a dangerous link in an email is to install a comprehensive antivirus with real-time protection. Real-time protection scans emails, files, and websites in real time for malicious links. It intercepts any dangerous files and downloads, like ByteFence Secure Browsing, and prevents them from infecting your computer.
Secure Your Wireless Network and IoT Devices
In addition to keeping your software updated and running real-time protection on your computer, you also need to secure your wireless network and internet of things (IoT) devices, like home security systems and digital appliances. If you fail to do this, cybercriminals can hack your network and IoT devices, steal your data, and even take control over your devices.
You should always try to avoid using a public Wi-Fi network, but if you have no choice, use a virtual private network (VPN) any time you connect to an unsecure network (I recommend ExpressVPN). A VPN protects your data with 256-bit encryption (which is one of the best out there) and provides you with extra anonymity online.
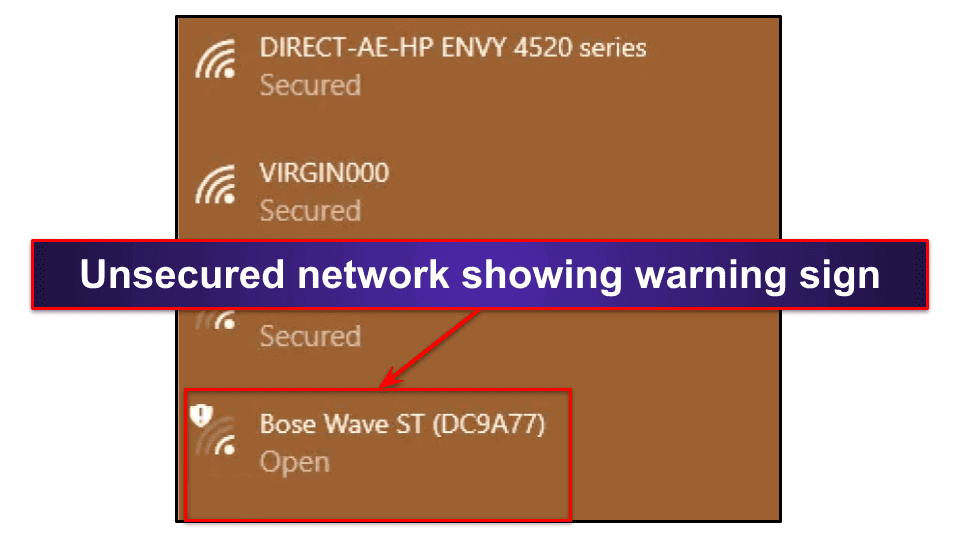
You can recognize a secure wireless connection by the word “Secured” written underneath the name of the network. Unsecured networks will show a shield icon with an exclamation mark, and they’ll have “Open” written underneath the name — always connect to a VPN when you use an unsecured network.
If your Wi-Fi network isn’t secure, you need to set a password. To learn how to do this, type your router’s model number and brand name into a Google search or check your router’s instruction manual.
You need to also secure your IoT devices with a password — without one, cybercriminals can access your devices and monitor your home activity. Follow the same steps to set up a password for your IoT devices that you took to set a password for your wireless network.
The best way to create secure passwords for your router and IoT devices is to install a good password manager like Dashlane or Keeper. A good password manager will help you create strong passwords that have up to 20+ characters, store your passwords in a secure vault that only you have access to, and make sure you never forget your passwords.
Download a Secure Antivirus Program
The last and most important step to securing your PC is to install a comprehensive and trustworthy antivirus suite. There are a ton of antiviruses on the market to choose from, but many lack essential security features. So, it’s hard to know which antivirus program is right for you without doing the proper research. However, we’ve done all of the hard work for you.
Here’s our list of the top 10 antiviruses in 2024.
Norton is my favorite antivirus, and it has the following features to keep your device safe and secure:
- Real-time protection. Activity scans your computer and stops you from accidentally downloading any dangerous files.
- Firewall. Monitors your inbound and outbound traffic, stopping unauthorized access to your network.
- Virtual private network (VPN). A VPN changes your IP address with one from a new location, enabling access to geo-restricted content and protects your online privacy.
- Parental controls. Allows you to set a limit on your child’s screen time and filter what websites they can visit.
- Identity theft protection (US only). Looks for unexpected changes in your credit report and monitors your personal data to make sure it doesn’t end up on the dark web.
- Cloud backup. Creates backup copies of your important files so that they remain accessible if you suffer from a ransomware attack.
Frequently Asked Questions
What is ByteFence Secure Browsing?
ByteFence Secure Browsing is a PUP that will steal your data and change your default search settings. It sells itself as a safe search engine, but you shouldn’t trust it. Instead of providing extra security while you browse the web, ByteFence Secure Browsing redirects you to suspicious websites and profits from your search history by tracking your data and sending you targeted ads. If you want a secure browser extension, I recommend using Norton’s Safe Web browser extension.
Is ByteFence Secure Browsing safe to use?
No, ByteFence Secure Browsing steals your data and uses this information to spam you with annoying ads and pop-ups. You should never download ByteFence Secure Browsing, but if you do (or add it by accident), follow these steps to remove it from your device.
Why is ByteFence Secure Browsing not uninstalling?
ByteFence Secure Browsing can’t be uninstalled through the Windows 10 control panel. Since ByteFence utilizes a web browser extension, you will have to uninstall it through your web browser following our steps that are outlined above.
Once you’ve uninstalled ByteFence Secure Browsing, you need to run a full-disk virus scan with a comprehensive antivirus like Norton 360 to make sure you don’t have any further infections. You can purchase Norton 360, run the full scan, delete any malware files the scan detects, and then request a full refund with Norton’s 60-day money-back guarantee.