SafetyDetectives Cybersecurity Team
Updated on: March 20, 2024
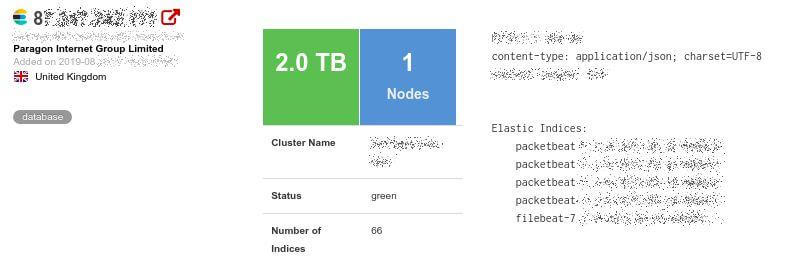
The security research team at Safety Detectives has uncovered yet another data leak worth 2 terabytes of data hosted on an Elastic Server. Affecting savvy shoppers in both India and the U.K., sister sites Pouringpounds.com and Cashkaro.com – both of which belong to Pouring Pounds Ltd. – have provided the dark web with yet another source of full PII and account access to up to 3.5 million individuals.
What’s Being Leaked?
Head of Research, Anurag Sen, and team found that the cashback and voucher websites Cashkaro.com and Pouringpounds.com have both made available key details about their active users:
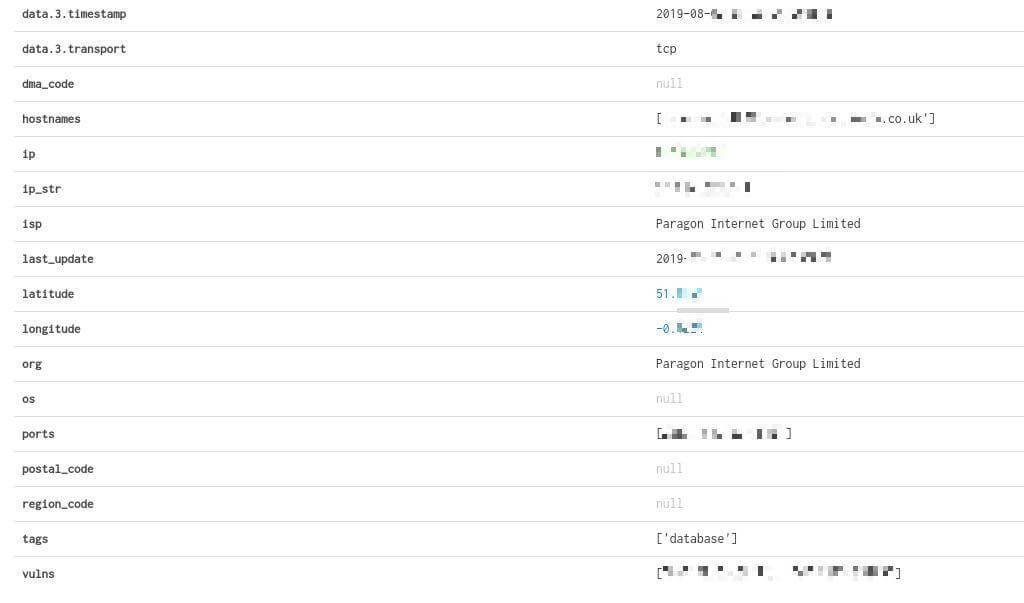
We created an account to test the visibility. Here’s our data. No bank account was connected to the account.
The leak on Pouringpounds.com database includes data related to PouringPounds users, such as:
- Full names,
- Phone numbers,
- Email addresses,
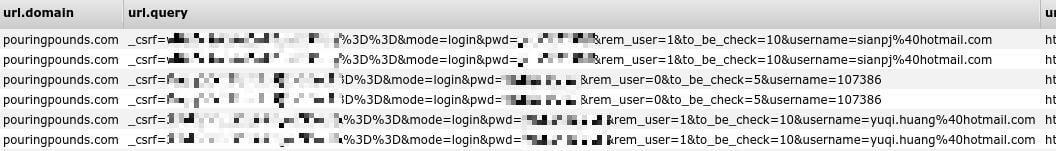
- Login credentials to the platform
- Username
- Plaintext password
- Bank details linked to account from the site
- Name of account holder
- Bank name
- Account number
- Sort code (routing numbers)
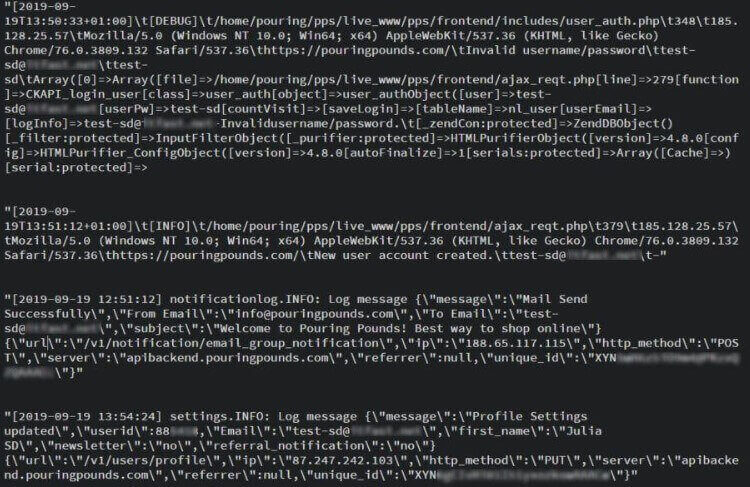
- Emails from Pouringpounds to their users,
- IP addresses
As well as Cashkaro.com’s user, including:
- Full names,
- Phone numbers,
- Email addresses,
- Login credentials to the platform
- Username
- Plaintext password
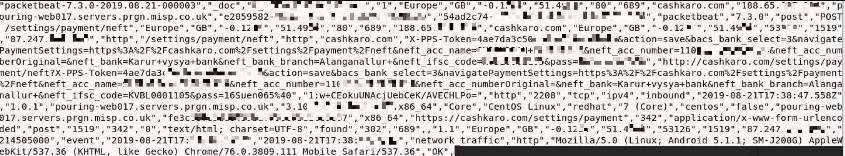
- Bank details linked to account from the site
- Account holder name
- Bank name
- Branch
- Account number
- IFSC code
- Bank account related password (we cannot be certain what it is used for, but unencrypted passwords are being linked with the bank details)
- Emails from Pouringpounds to their users,
- IP addresses
Editor’s Note: As previously mentioned, the data found seems to be related to ‘active’ users – those who have logged in only in recent months.
The elastic server was publicly exposed without any password protection. Searching at a specific port, anyone could find it easily and take advantage of it maliciously. From what we can see, it was exposed since August 9th, 2019.
On PouringPounds.com – a site with over a million users – the username and plain-text passwords stored mean that anybody could easily take over the entire account, including the amount of credit they have in their wallet on the site.
A bad actor could easily open an account and find the associated cashback credit – available and ready to be transferred to any Paypal address easily. All you need to execute such a transaction would be the password which, again, we found available in plain text.
For CashKaro.com – a site with over 2.5 million registered users – we also found plain text passwords and their associated accounts. Many logs containing bank account details and links to said accounts were found, as well; this is information used during the checkout process.
Two whole terabyte of personally identifying and financial/payment data of up to 3.5 million people is a very serious exposure by any measure.
Take into consideration that many web users often use the same password across all sites. With unencrypted passwords and their associated emails and additional account details, this can impact individuals in countless ways.
The leak was first spotted at the end of August 2019, but first investigated by our security researchers on September 2nd. We disclosed the leak to the owner of the data, and our Head of Research made multiple attempts to contact them, including via Twitter (but the concern was apparently never forwarded to their own security team). We at Safety Detectives contacted them on September 19th and received a reply on September 21st, and the database leak was closed the same day.
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you’re not a victim of attacks – cyber or real world – if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you’re on is secure (look for https and/or a closed lock).
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.).
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecure WiFi networks
Find out more about the best tips to prevent phishing attacks, and how to avoid ransomware.
About Us
SafetyDetective.com is the world’s largest antivirus review website. The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats, while educating organizations on protecting their users’ data.
For more info about our work, read our previous reports regarding a Job Portal Database Exposed or the Personal Data (Incl. SMS & Calls) of Mobile Loan App Users in China Left OPEN for ALL to See.
Published on: Oct 16, 2019