Kamso Oguejiofor-Abugu
Updated on: January 4, 2024
Short on time? Here’s the best antivirus to protect your phone against text exploits in 2024:
- 🥇Norton Mobile Security — Excellent features for mobile protection, including malware scanner (Android only), SMS spam filter, web protection, a Wi-Fi network monitor, a VPN, and a password manager. It also offers a generous 60-day money-back guarantee.
As cybercrime becomes more sophisticated, so do the methods of attack. One such method involves simply sending a text message. Seeing an odd text message on your personal phone can be alarming, and rightly so. A malicious text message, often disguised as a legitimate communication, can pave the way for cybercriminals to access your personal data.
But fear not, this is not an issue if you follow the right steps. One of these steps involves using a quality antivirus like Norton — a premium antivirus software with an excellent track record in protecting mobile devices from all sorts of cyberattacks. Whether it’s a malicious text message or sophisticated spyware, Norton can offer a powerful defense against it.
How Cybercriminals Hack Your Phone By Texting You (& Other Hacking Methods)
Cybercrime has evolved significantly over the years, with hackers adopting more sophisticated techniques to infiltrate our digital lives. Here, I’ll delve into various ways that cybercriminals can hack your phone, including smishing, spyware, and unsecured public networks, among others.
Zero-Click Text Exploits
These exploits are especially dangerous, as they don’t require user interaction to be successful. A good example is an exploit called Operation Triangulation. This targeted campaign, launched in 2019, uses zero-click exploits via the iMessage platform, resulting in the complete takeover of the user’s iPhone.
Another case is the zero-click vulnerability that was exploited in WhatsApp, a popular messaging app. It allowed spyware to be installed on targeted phones using the app’s voice call function. Even if no one picked up the call, the malware would be installed, and the call deleted from the device’s log.
Such exploits are complex and usually state-funded. Mobile apps present an enticing vector of attack to cybercriminals, who continually seek new exploits and vulnerabilities. Therefore, awareness and adopting strong security measures are essential to protect against these threats.
Smishing & Phishing
Smishing is a cyber attack that involves sending text messages under false pretenses to trick individuals into revealing sensitive information. Typically, the text message will appear to come from a trusted source, such as your bank or a familiar website, and ask you to confirm your account information or PIN. Bitdefender contains a scam alert feature that automatically looks for smishing messages and moves them to your junk folder upon detection — it’s a good defense against this type of attack.
Phishing is similar to smishing, but it occurs through emails rather than text messages. The email appears as official communication from a trusted source to lure you into revealing personal details.
Social Engineering Messages
Social engineering involves manipulating you into sharing confidential information or performing actions that compromise your digital security by triggering an emotional response. Cybercriminals craft messages that create fear or inspire curiosity to fool you into revealing passwords, downloading malware, or making fraudulent transactions. Awareness and skepticism of unusual requests or messages can significantly mitigate these risks.
Hacked Contacts
Your contacts’ accounts can be hacked and used to target you with malicious content, such as malware-infected files or phishing links. Since these messages appear to come from a trusted source, they can be particularly effective. Always approach unexpected messages or attachments with caution, even if they’re from known contacts. If you suspect someone you know has been hacked, alert them to the issue.
AirDrop & Nearby Share
Features like AirDrop (iOS) and Nearby Share (Android) can also be exploited by attackers. Hackers can send unsolicited files containing malicious software to a nearby iPhone or Android device. Once the software is installed on your phone, it could compromise your device and steal your personal information. It’s best to adjust your settings to allow file sharing only from known contacts.
Messaging Apps
Popular messaging apps can be targeted by hackers to distribute malware or spyware. Incidents such as the NSO Group’s Pegasus spyware exploiting WhatsApp underscore this vulnerability. Regularly updating these apps and avoiding clicking on suspicious links can help mitigate these threats.
Malicious Calendar Invites
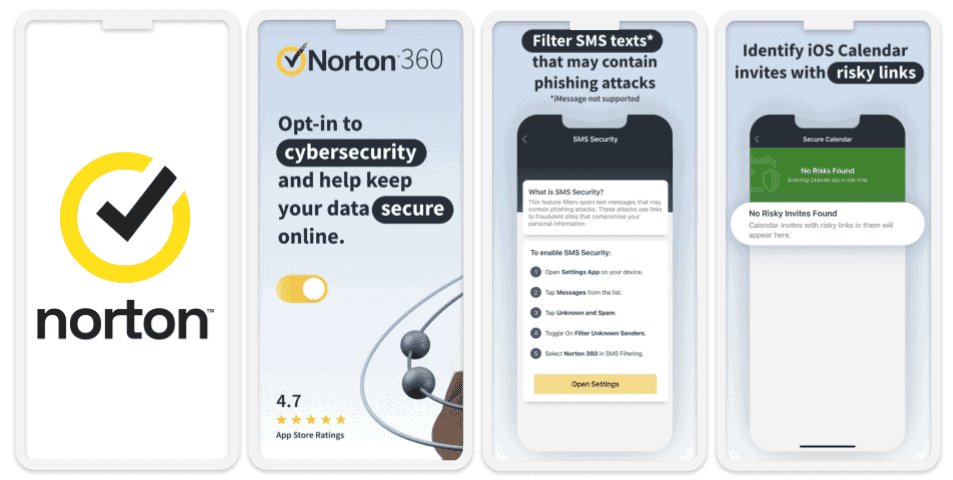
Calendar apps have become a new avenue for phishing attacks. Hackers can send malicious invites, which, once accepted, can lead to the installation of malware on the device or the theft of personal data. Norton provides a Secure Calendar feature for iOS that blocks such invites, keeping your iPhone safe from phishing attempts that arrive in the form of iOS calendar notifications. Likewise, Bitdefender’s scam alert feature can scan your Apple calendar and prevent you from getting these malicious calendar invites.
Unsafe Apps
Unsafe apps are another method cybercriminals use to hack your phone. Downloading and installing apps from unofficial sources or without thorough vetting can introduce malicious software to your device. A good mobile antivirus can help protect your phone from malicious apps. For instance, Norton’s App Advisor scans apps that are about to be downloaded to check for anything suspicious, and Bitdefender’s App Anomaly Detection continuously monitors app activity on your phone and alerts you if any apps start behaving strangely.
Unsecured Networks
Unsecured public Wi-Fi networks are common places for hackers to stage their attacks. These networks often lack the security measures to prevent unauthorized access, making it easy for hackers to intercept the data being transmitted over the network. If you want to use public Wi-Fi, I recommend using a good VPN like ExpressVPN to encrypt your data and protect it from hackers.
Zero-Day Attacks
Zero-day attacks exploit previously undiscovered vulnerabilities in software. They’re particularly dangerous because they occur before developers have had a chance to create a patch. Keeping your devices and applications up-to-date is essential, as updates often contain patches for newly-discovered vulnerabilities. However, it’s also crucial to be aware of the latest threats and to use a comprehensive antivirus like Norton, which provides protection against zero-day attacks and other threats.
How to Protect Your Phone From Text Exploits & Other Threats
Note: If you suspect your phone might already be hacked, here are a number of steps you can take to rectify the situation.
Protecting your mobile device from hackers is not a daunting task if you’re vigilant and proactive. Here are some steps you can follow to ensure your device, be it iOS or Android, remains secure.
Step 1. Install an Effective Antivirus App
This should be your first line of defense. Quality antivirus software can help protect your device from malware, spyware, and phishing attempts. It can also alert you when you download a potentially unsafe app or visit a dangerous website. My favorite antivirus app for mobile devices is Norton Mobile Security.
Step 2. Use a VPN (Virtual Private Network)
A VPN helps to secure your internet connection and protect the data you send and receive online. VPNs create a secure, private tunnel between your device and the internet. All your internet traffic is sent through this secure connection, which protects it from anyone trying to intercept or spy on your activity. A VPN comes in especially handy when using public Wi-Fi, which is a common target for cybercriminals. I recommend ExpressVPN (it’s the best VPN in 2024).
Step 3. Enable Two-Factor Authentication (2FA)
2FA adds an extra layer of security to your online accounts by requiring two types of identification before you can log in. The 2FA could be in the form of biometrics (fingerprint, face ID, etc), time-based one-time passwords (TOTPs), or hardware authentication devices like Yubikey, for example. Enabling 2FA for your accounts means that even if a hacker gets hold of your password, they’ll have a hard time accessing your account without the second factor.
Step 4. Keep Your Software Updated
Regularly updating your phone’s software is crucial, as most updates come with security patches that fix vulnerabilities hackers could exploit. You can easily update your phone via your device settings — you can also set up updates to occur automatically.
Step 5. Avoid Third-Party App Stores
Stick to trusted sources like the App Store for iOS and Google Play Store for Android. Third-party app stores may host apps that contain malware, and are best avoided.
Step 6. Uninstall Unused or Suspicious Apps
If you don’t use an app, it’s best to uninstall it. Also, if an app starts acting strangely (crashing, requesting unusual permissions, etc.), be sure to remove it immediately. Bitdefender’s App Anomaly Detection constantly monitors your phone apps for any suspicious activity, so you always know which apps you need to delete.
Step 7. Check App Permissions
Be wary of apps that ask for permissions that don’t seem necessary for their functionality. An app should only have access to the components of your phone that it needs to function. To check permissions on iPhone, go to Settings > Privacy & Security, then click on the Apple app in question. Similarly, for Android, go to Settings > Privacy, then adjust the permission settings there. Regularly review these settings to ensure no unnecessary access is granted.
Step 8. Use a Password Manager
A password manager generates and stores complex passwords for your various accounts, making it harder for hackers to gain access. I highly recommend 1Password — it comes with unbreakable security, user-friendly apps for all platforms and devices, and several useful additional features.
Best Antivirus Apps for Protecting Your Phone (Android & iOS) in 2024
Quick summary of the best antiviruses for smartphones in 2024
- 🥇 1. Norton. Best antivirus for smartphones in 2024.
- 🥈 2. Bitdefender. Advanced malware protection for mobile devices.
- 🥉 3. TotalAV. Intuitive interface for smartphone users.
🥇 1. Norton — Top Choice for Smartphone Protection in 2024
Norton Mobile Security is the best antivirus for mobile devices in 2024. It provides excellent malware protection using machine learning, heuristic analysis, and a massive malware directory to detect all types of threats on your phone. However, this feature is not available for iOS devices, mainly because they can’t get viruses.
I tested Norton’s malware detection by installing several malware files on my Android, including spyware, keyloggers, viruses, worms, and ransomware, and it removed every single file.
Norton also provides:
- App Advisor (Android only).
- SMS spam filter.
- Web protection.
- Wi-Fi network monitor.
- VPN.
- Safe Web & Safe Search.
- Device security.
- Secure calendar (iOS only).
- Password manager (separate app).
- LifeLock identity theft protection (separate app).
- And more…
I am a fan of Norton’s App Advisor, which scans the apps on your phone as well as the ones about to be downloaded. The App Advisor provides details such as the privacy risks and battery consumption of each of your phone’s apps. It also lets you know which apps were installed in the last 30 days.
Another tool I like is the SMS spam filter. It blocks unsafe smishing texts on your phone and, unlike the App Advisor, it’s available for both iPhones and Android devices.
Norton also has really good web protection. I particularly like the Safe Web browser extension, which provides protection against phishing sites, community reviews for suspicious websites, and an Intrusion Prevention System (IPS) for safe online transactions. During my tests, Safe Web detected the majority of the phishing sites I visited on my Android phone, including ones that Chrome and Firefox missed.
Norton Mobile Security covers 1 mobile device (iOS or Android) and costs $17.99 / year*. However, if you need protection for more devices, I recommend Norton’s best value plan, Norton 360 Deluxe ($49.99 / year*), which covers up to 5 devices including Windows, Mac, iOS, and Android. All plans come with a generous 60-day money-back guarantee.
🥈2. Bitdefender — Advanced Protection Against Text Message Hacks
Bitdefender Mobile Security is an excellent mobile security solution against text message hacks and other types of threats. With an impressive range of features, it ensures robust protection for both Android and iOS devices.
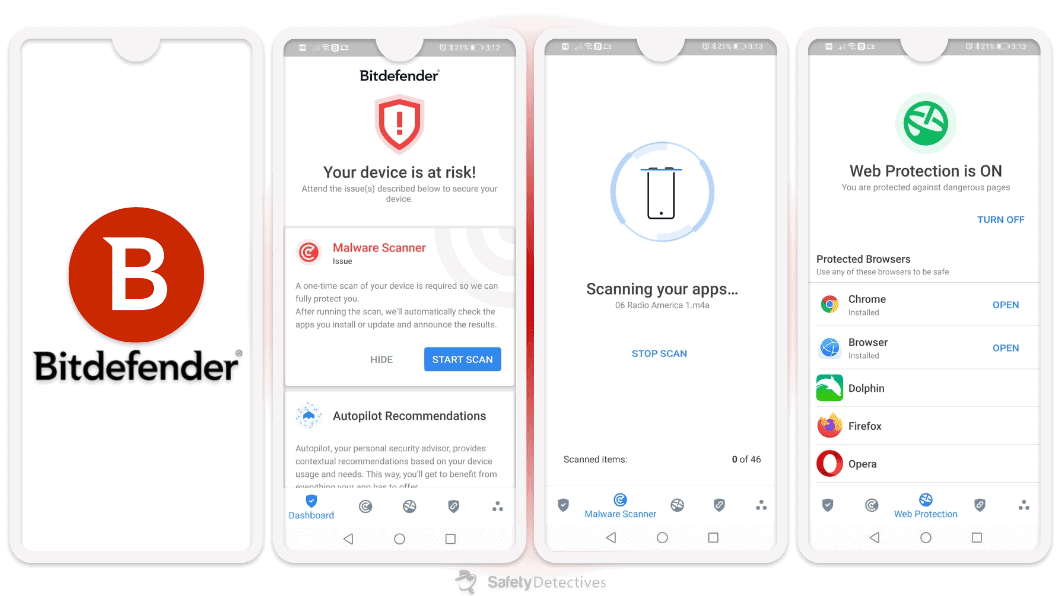
Bitdefender’s malware scanner (available only on Android devices) is lightweight and cloud-based, and it uses a huge malware directory and machine learning to detect all types of malware. It performed excellently in my tests, detecting every single malicious file I hid on my Samsung phone.
Other notable features include:
- Web protection.
- App Anomaly Detection.
- Autopilot (automatic security recommendations).
- App lock.
- Scam alert.
- Anti-theft protection.
- Data breach monitoring (email only).
- VPN (200 MB/daily).
- Smartwatch compatibility.
Bitdefender’s scam alert is an excellent way to protect your phone from malicious texts. It automatically scans your SMS folder and messaging apps for messages containing suspicious links and moves any it finds to your junk folder. Honestly, this is pretty much all you need to stop someone from hacking you via text.
I really appreciate Bitdefender’s web protection, too. During my tests, I visited dozens of malicious sites and Bitdefender blocked all of them, including websites that Chrome’s built-in protections failed to detect.
I also like Bitdefender’s App Anomaly Detection feature — it’s a bit different from Norton’s App Advisor, as it constantly monitors all your apps on an ongoing basis (which Norton doesn’t), and alerts you if it detects any suspicious behavior. This is a really handy feature — I only wish it was available on iOS devices and not just on Android.
Bitdefender Mobile Security covers 1 iOS or Android device and costs $17.49 / year. However, you can get a more comprehensive plan with Bitdefender Total Security, which provides coverage for 5 Windows, Mac, iOS, or Android devices for $49.99 / year. Plus, all plans are backed by a risk-free 30-day money-back guarantee, so there’s no risk in trying Bitdefender out.
Read the full Bitdefender review
🥉3. TotalAV — User-Friendly Antivirus With Powerful Malware Scanner
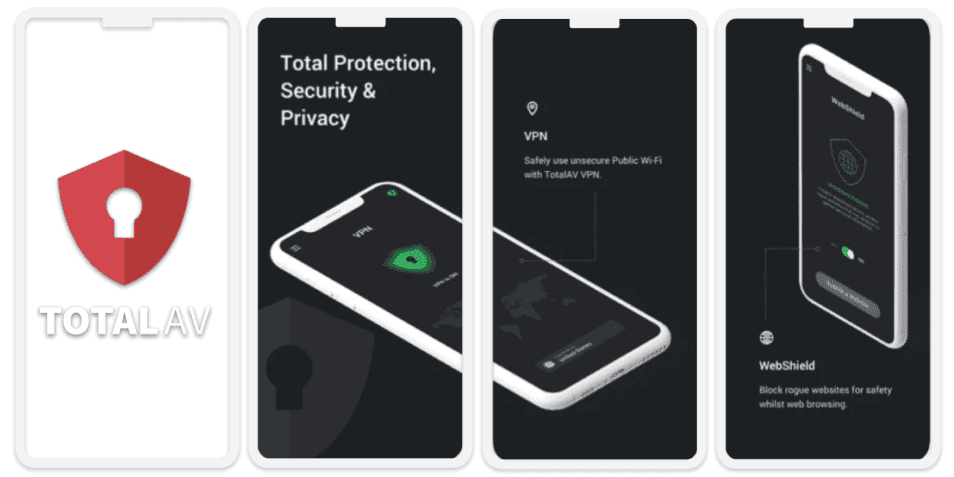
TotalAV is a user-friendly antivirus software that provides top-notch malware protection, excellent device optimization tools, and useful extras. As with Norton and Bitdefender, the malware scanner is only available on Android. When I tested it out, it was able to detect almost 100% of the malware files I downloaded onto my Android phone.
Some of TotalAV’s key features include:
- Anti-phishing.
- Wi-Fi checker.
- VPN.
- Device tune-up.
- Secure in-app browser.
- Data breach monitoring.
TotalAV’s VPN for mobile users is pretty good — it’s very effective for when you’re using a public Wi-Fi network on your phone, as it can prevent hackers from stealing your personal data. During my tests, TotalAV’s VPN provided encrypted access to servers worldwide and fast speeds — in fact it’s the best antivirus-bundled VPN on the market.
I was impressed with TotalAV’s anti-phishing tool, WebShield. It’s very effective at blocking phishing sites and other online malware distributors, so even if you happen to click on a phishing link in a text message, TotalAV will block the site completely. I tested WebShield out, and it worked very well, detecting more phishing sites than Chrome and Firefox. However, competitors like Norton provide slightly more advanced anti-phishing protections.
TotalAV doesn’t have a separate mobile plan like Norton and Bitdefender, so you’ll have to buy it as a bundle with other devices. I recommend TotalAV Internet Security ($39.00 / year), as it provides all the tools you need to keep your phone safe from smishing (and other types of malware attacks), such as a malware scanner, real-time protection, anti-phishing protection, a VPN, and more. It also comes with a 30-day money-back guarantee.
What to Do If Your Phone Has Been Hacked
- Disconnect from the internet: If you suspect you’ve been hacked, turn off your Wi-Fi and mobile data immediately. This can help prevent further data from being sent to the hacker.
- Backup important data: Make sure that you save any important data to a separate device or cloud storage. This may include photos, messages, or other important documents.
- Delete unrecognized apps: If you spot apps that you didn’t install yourself, delete them immediately. Unknown apps could contain malicious software.
- Scan for malware: Use a reputable antivirus app like Norton to scan your phone for any malware. This can help identify and remove any harmful software.
- Update your operating system and apps: Software updates usually include security patches which can help fix vulnerabilities that hackers may exploit.
- Change passwords: Change the passwords on your accounts, especially if you’ve noticed any suspicious activity. Always choose strong, unique passwords. Using a secure password manager like 1Password can help create and store complex passwords securely.
- Enable two-factor authentication (2FA): If you haven’t done so already, set up 2FA for your accounts. This adds an extra layer of security.
- Review app permissions: Go through the apps on your phone and check what permissions they have. If an app has more permissions than it needs, it’s a good idea to revoke them.
- Factory reset: If all else fails, consider doing a factory reset of your phone. Be aware, this will delete everything on your device, so ensure you’ve backed up your data prior to the reset.
- Alert your contacts: Notify your contacts that your phone was compromised to prevent them from becoming victims too. Advise them not to open suspicious links or messages they might have received from you.
How to Tell If Your Phone Has Been Hacked
- Unusual battery drain: If your phone’s battery is draining much faster than usual without any significant change in usage, it might be due to hidden malware operating in the background.
- Increased data usage: A sudden spike in data usage can be another red flag. Many forms of malware tend to consume high data bandwidth.
- Erratic behavior: Unexpected shutdowns, crashes, or slow performance can be indicative of a cyber attack. If your phone is acting strange, it’s always best to investigate and to perform a scan with a reliable antivirus.
- Suspicious apps: If you notice apps that you didn’t install, it could be a sign of a hack. Some malicious apps disguise themselves as regular apps but operate behind the scenes to extract your data. You should delete these apps immediately and run a scan with your mobile antivirus.
- Pop-up ads: An excessive number of pop-up ads might indicate adware — a type of malware that bombards users with unwanted ads.
- Unusual phone bills: Unauthorized charges on your phone bill for calls or messages you didn’t make can be a sign of hacking.
- Eavesdropping signs: If your phone exhibits signs of eavesdropping, like weird noises during calls or the phone lighting up when not in use, it might be compromised.
Can Someone Hack My Phone By Calling Me?
Your phone can potentially be compromised via a simple phone call, although it’s relatively rare. The Pegasus software from the Israeli firm NSO Group is a notorious example of a “zero-click” exploit, which can infiltrate your device without requiring you to click a link, download a file, or answer a call. Once installed, Pegasus can monitor calls, read texts, and even control your phone’s camera and microphone.
Beyond sophisticated software like Pegasus, there are more common phone-based scams that rely on social engineering techniques. Fraudsters might pose as trusted individuals or organizations, tricking you into sharing sensitive personal information or making unwise financial decisions.
A concerning trend that emerged recently is AI voice scamming. In these scams, artificial intelligence is utilized to create realistic voice simulations, mimicking the voices of victims’ loved ones to persuade them into transferring funds under the premise that they’re helping a relative in distress. In 2022, over 5,100 cases of such impersonation phone scams were reported in the United States, with victims collectively losing over $11 million.
These threats are becoming increasingly sophisticated — as such, maintaining vigilance and skepticism towards unexpected phone calls is crucial. Always verify the identity of the caller independently before sharing any sensitive information or money, especially when the request is urgent or seems out of character.
Lastly, reporting these incidents to the relevant authorities is an important step in combating these scams and holding the perpetrators accountable.
Apple iMessage No-Click Text Exploit
Kaspersky, a Moscow-based security firm, reported an advanced cyberattack that utilized a “clickless” exploit via iMessage to compromise several employees’ iPhones. This stealthy malware, termed “Triangulation,” gathered sensitive data including microphone recordings, photos, geolocation, and more. The “clickless” exploit operated by sending iMessage texts with a malicious file, exploiting vulnerabilities in iOS and installing the APT (advanced persistent threat) malware.
The spyware installation is hidden, requiring no user action. Infected devices show data usage lines mentioning a process named ‘BackupAgent,’ and compromised iPhones can’t install iOS updates. The most recent version targeted was iOS 15.7. Kaspersky researchers detected the attack through unusual activity on their corporate Wi-Fi network, with traces of this campaign going back as far as 2019.
Most users are unlikely to fall victim to a targeted attack of this kind, but to protect against such exploits iPhone users should always maintain the latest software updates and promptly install any emergency security updates.
NSO Group’s Pegasus Phone Spyware Explained
Pegasus is a spyware developed by the Israeli cybersecurity firm NSO Group. Initially discovered in 2016, it’s designed to infiltrate smartphones, both iOS and Android, to turn them into surveillance devices. Once installed, Pegasus can access sensitive data, including messages, emails, and contacts, and can even control the phone’s microphone and camera for real-time surveillance.
Pegasus works by exploiting undiscovered weaknesses, also known as ‘zero-days,’ in operating systems. These weaknesses enable the spyware to circumvent the system’s security measures and implement itself without any user engagement. Pegasus is usually disseminated through phishing attacks by means of SMS, WhatsApp, or emails that trick users into clicking on a harmful link, although it can be installed via ‘no-click’ attacks as well.
Pegasus has been implicated in various controversies due to its misuse. Despite NSO Group’s claims that the tool is sold only to government agencies to fight crime and terrorism, there have been several instances of misuse, such as targeting journalists, activists, and opposition politicians. While this insidious technology has been used unethically by certain regimes, the likelihood of the average user’s device being targeted by Pegasus is very low. Sophisticated zero-day attacks such as Pegasus are typically aimed at specific high-profile targets.
However, it’s still crucial to maintain good cybersecurity practices and stay alert to protect your devices and sensitive data.
Frequently Asked Questions
Can you be hacked by replying to a text?
No, you cannot be hacked simply by replying to a text message. However, if the text contains a link, clicking on it could direct you to a malicious website designed to steal your personal information, or it could automatically download malware onto your device. Downloading files sent through text messages can also endanger your device.
Some hackers may also use social engineering techniques in their text messages to trick you into providing sensitive information. So, it’s important to be cautious and avoid interacting with suspicious messages, particularly those from unknown numbers or contacts.
Can someone hack my phone by texting me on WhatsApp?
No, simply receiving a message on WhatsApp cannot result in your phone being hacked. However, similar to standard text messages, there can be risks associated with any links or files that may be sent in a message. Clicking on a suspicious link or downloading a malicious file could potentially expose your device to harmful software. Always ensure that messages, files, and links you receive are from trusted sources, and regularly update your applications and device software for optimal security.
Can someone spy on my text messages?
Yes. Spyware can be stealthily installed on your phone, allowing someone to read your text messages remotely. These malicious apps can be installed without your knowledge and can even disguise themselves as everyday apps. To protect yourself, install a robust antivirus like Norton Mobile Security that can detect and remove spyware. Additionally, always avoid clicking on suspicious links, and never install apps from untrusted sources.
Can someone hack my phone by texting me a photo?
No, merely receiving a text message with a photo cannot result in your phone being hacked; however, downloading the image can. This is typically achieved through a method known as image steganography, which involves hiding malicious code within the digital data of an image file. If the image is opened or downloaded, it can potentially compromise your device. To guard against this, always exercise caution when receiving image files from unknown or untrusted sources.
Can someone hack my phone if I open a text message?
No, merely opening a text message on your phone isn’t typically risky, but the actions that may follow could be. If you click on links or download attachments, you may inadvertently expose your device to hackers. Always use sound judgment when receiving texts from unknown numbers, and don’t interact with suspicious or uninvited messages. Installing a trusted mobile security app like Norton can also provide an additional layer of protection against potential threats.