The tides of the jailbreak community forever changed for the better on Friday when hacker and security researcher @axi0mX released checkm8, the first publicly-released bootrom exploit for iOS-powered devices since the iPhone 4 in 2010. Captivatingly, checkm8 works on a significant number of handsets ranging from the antiquated iPhone 4s to the not-so-old iPhone X.
Checkm8 is, in and of itself, an exploit. That said, it’s not a jailbreak, but rather a powerful tool that jailbreak developers could use to devise a USB-based tethered or semi-tethered jailbreak tool for A5-A11 devices. Given how recently checkm8 was released, it should come as no surprise to anyone that public jailbreak tools don’t yet utilize the exploit, but that hasn’t stopped some talented hackers from flexing their l33t dexterities:
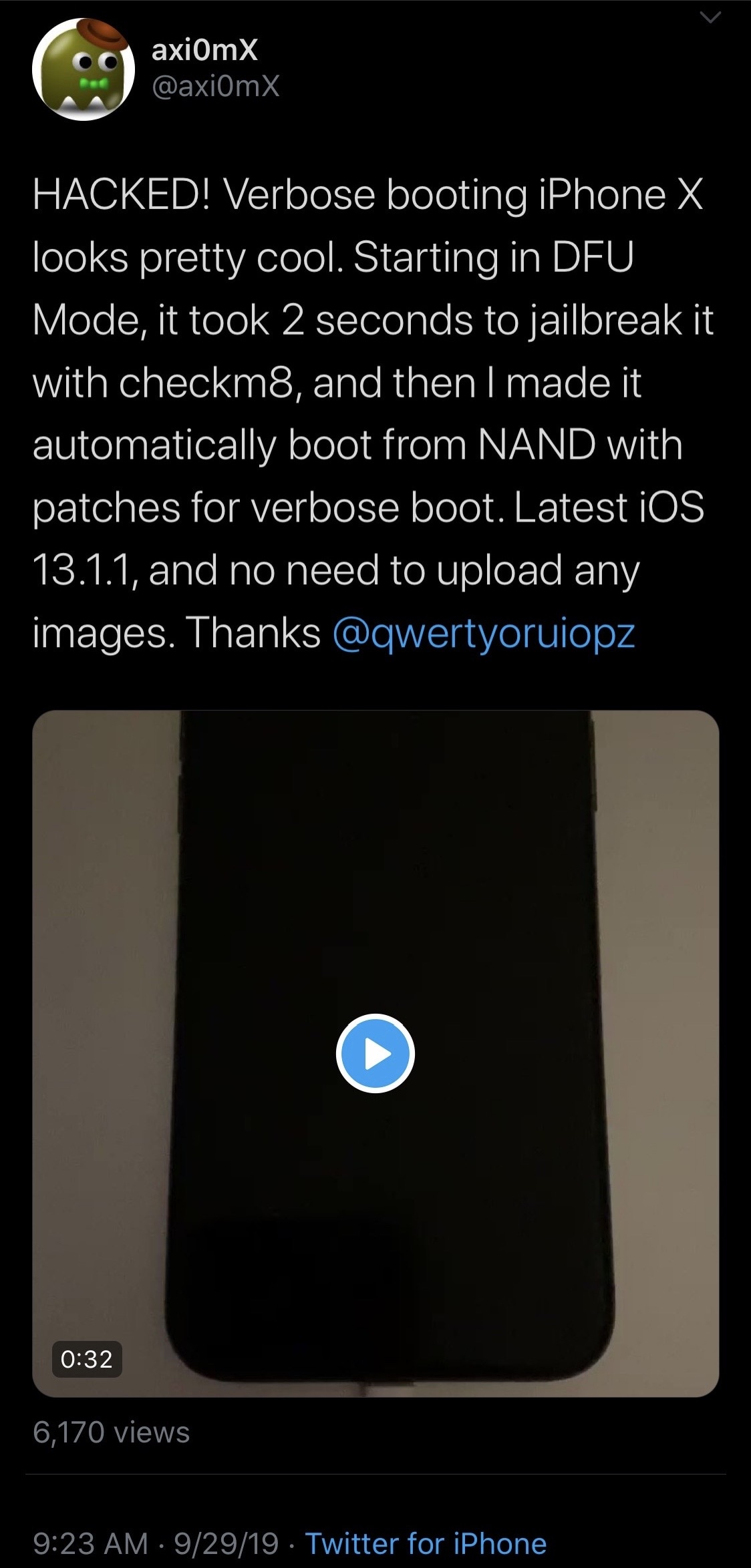
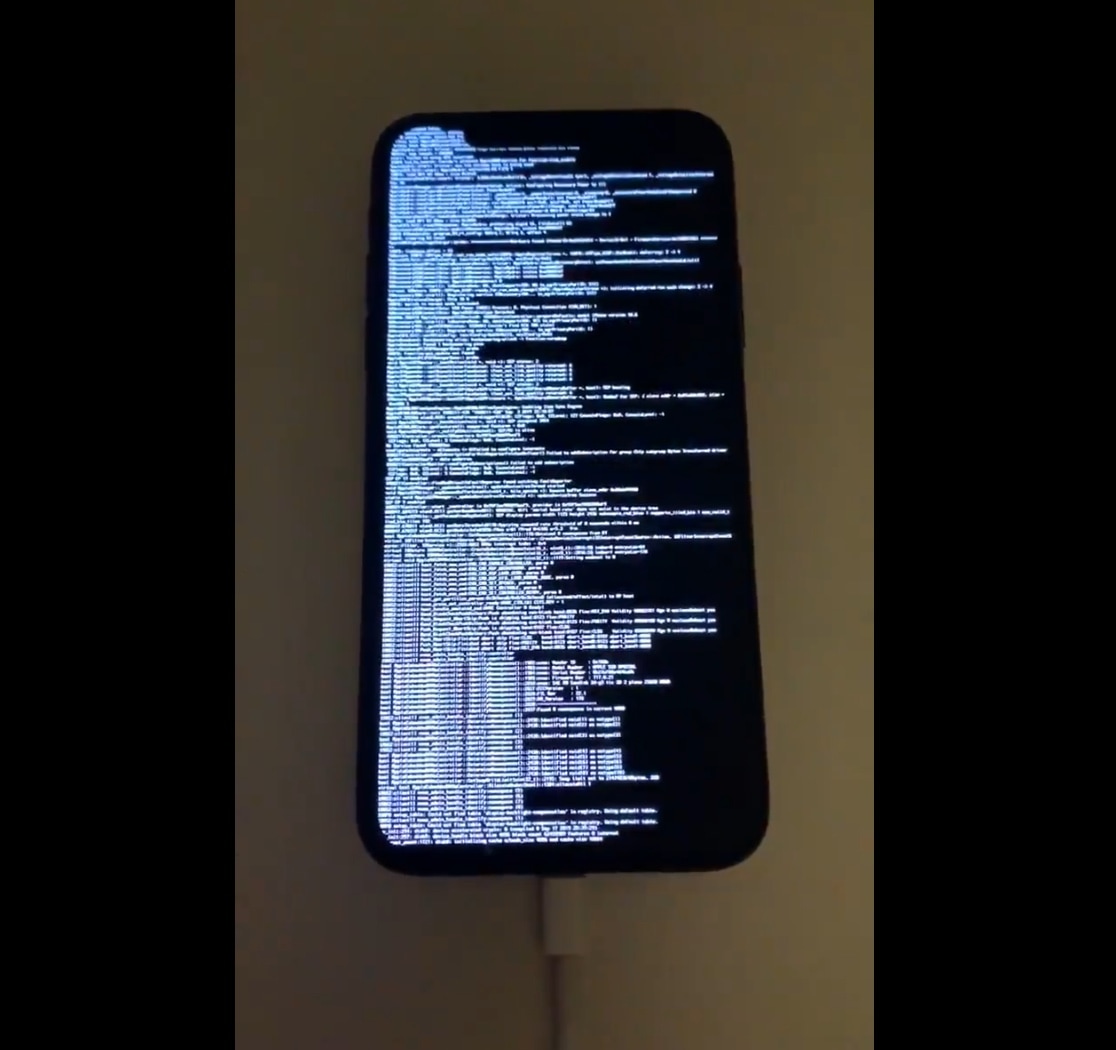
From what we can gather, famed hacker and Yalu jailbreak creator Luca Todesco has spent some time playing around with the new checkm8 bootrom exploit – at least long enough for @axi0mX to tease a nostalgic verbose boot screen (black background with scrolling white text) on an A11-equipped iPhone X. Click here to view the video.
Citing @axi0mX’s Tweet, checkm8 managed to jailbreak the showcased iPhone X in a matter of just two seconds, after which it displayed the verbose boot screen. Perhaps more importantly, the handset in question is purportedly running iOS 13.1.1, which is the latest iteration of Apple’s mobile operating system for iPhone, iPad, and iPod touch to date.
It’s worth noting that because checkm8 is a bootrom-based hardware exploit, Apple can’t patch it with a software update. Instead, Apple would have to recall all of its devices and install updated hardware with a patch to fix this, which is utterly unfeasible. For this reason, checkm8 just about guarantees the jailbreakability of A5-A11 devices for their entire lifetime, assuming a jailbreak developer is willing to consistently release and maintain jailbreak tools pertaining to it.
It remains to be seen when public jailbreak tools will adopt support for checkm8, but prominent hackers such as CoolStar and Pwn20wnd have already expressed oodles of interest in checking it out for their respective jailbreak tools. With that in mind, we expect that support could come in the not-so-distant future.
Are you excited about what the checkm8 exploit might bring to the jailbreak community? Discuss in the comments section below!




