Summary
- Authy is a 2FA app that recently suffered a data breach that exposed more than 33 million phone numbers.
- An unsecured API endpoint allowed threat actors to collect linked numbers.
- If you think your personal information might be among the 33 million leaked numbers, consider securing your accounts with 2FA and be wary of SMS phishing attacks.
Authy is an app that offers two-factor authentication, allowing users to keep their online accounts secure. Similar to one-time passwords, Authy generates 2FA codes that refresh every 20 seconds, and are stored on the cloud, preventing users from losing access to their codes in case they lose their phone.
The app is free-to-use, and works across platforms, including Android, iOS, macOS, Windows, and Linux. The only stain on its reputation is a 2022 security breach that affected its parent company, Twilio, which leaked information about 75 million users, though only 93 Authy users were targeted. Now, a new security breach affecting the 2FA app has reportedly given threat actors access to 33 million phone numbers registered on the app.

Authy has been hacked, here is how to protect yourself
One of the most trusted 2FA apps has suffered a breach, affecting a few unlucky individuals
Twilio pushed out an update for its Android and iOS app, alongside a news release on July 1, suggesting that it had “detected that threat actors were able to identify data associated with Authy accounts, including phone numbers, due to an unauthenticated endpoint.” The app updates served as a precaution for users, giving them access to the app’s latest security updates.
The culprit here was an unsecured API endpoint that allowed the threat actors to verify and collect numbers linked to Authy. The threat actors were reportedly able to feed the unsecured API a large list of phone numbers, and the endpoint only returned the numbers that were linked to Authy, alongside other account information.
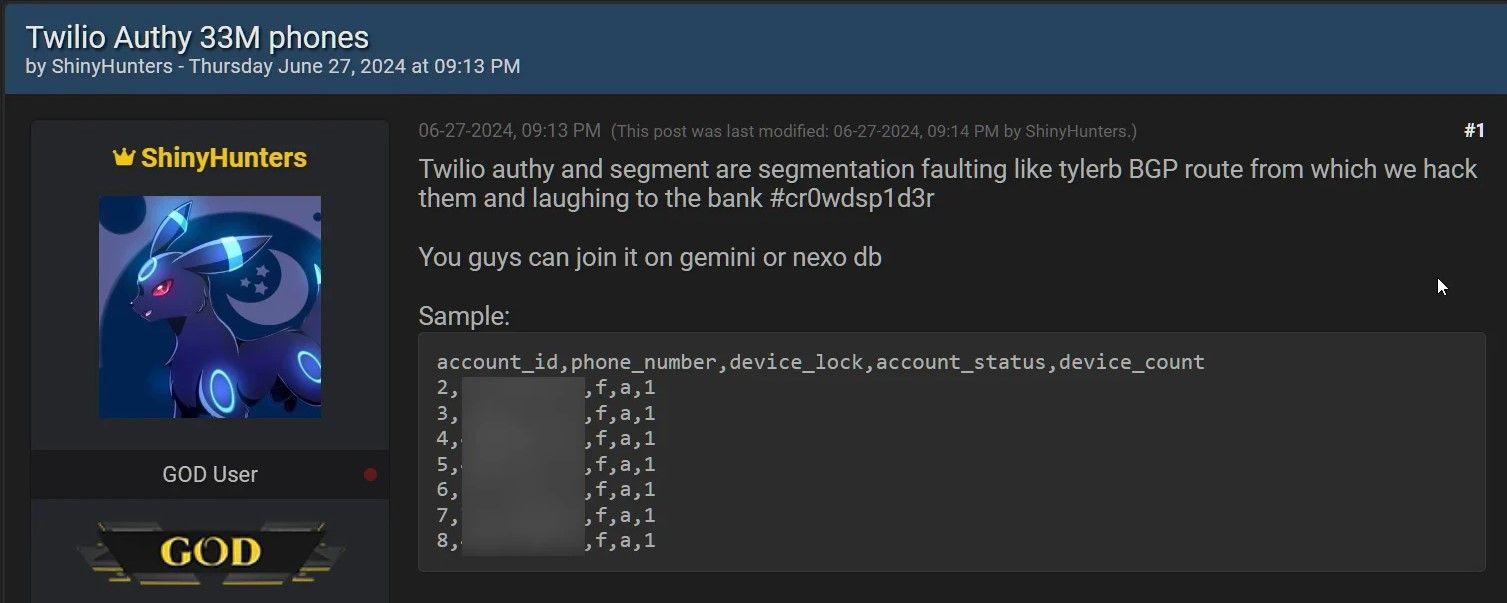
According to a Bleeping Computer report, a threat actor named ShinyHunters has been linked to the breach as they leaked a file containing over 33 million Authy-linked phone numbers, as suggested in the screenshot above.
The leaked data also included account IDs, alongside details about the account’s status and other linked devices. It’s worth noting that no passwords were leaked, but the leaked phone numbers and linked device information are enough for other threat actors to target Authy customers with sophisticated SMS phishing attacks.
Here’s what you can do as an existing Authy user
With access to your phone number, potential threat actors can either target you with SMS phishing attacks or attempt a SIM swap. The latter is essentially an illegal method where a threat actor convinces your carrier to transfer your phone number to a different SIM card, all while impersonating you. To convince the carrier, the threat actor might share your personal information, which they can find on social media or buy from the black market via leaks like the Authy one.
To prevent yourself from becoming a SIM swap victim, you can lock your SIM behind a passcode that you must enter every time you restart your device, or lock your phone number directly via your service provider.
Elsewhere, if you think your personal information might be among the 33 million leaked numbers, just be vigilant against suspicious SMS messages and ensure all of your social media, banking, or other sensitive apps are 2FA secured, and not authenticated via a text message. You should also update the Authy app. Updating the app wouldn’t make much of a difference now, but it will protect you if a threat actor attempts to breach the unsecured API endpoint again.