Apple’s brand-new Vision Pro spatial computer, the Cupertino-based company’s take on what’s basically a virtual reality headset (despite Apple’s attempt to not to have it branded as one), has only been available to the public for one day. But that hasn’t stopped talented hackers from working their magic on it.
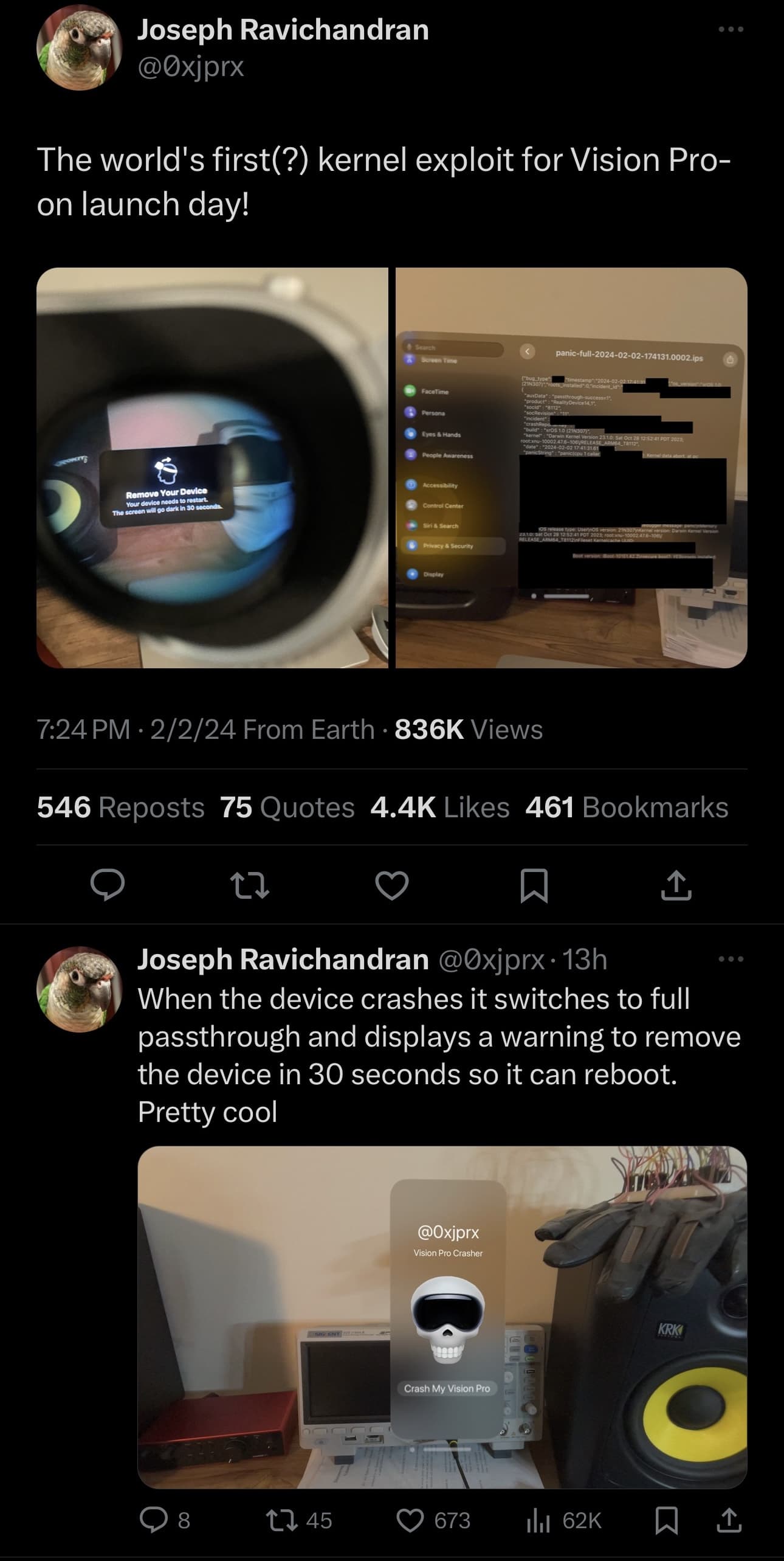
Joseph Ravichandran (@0xjprx), a PhD student studying Micro-architectural Security at Massachusetts Institute of Technology (MIT), took to X (formerly Twitter) late Friday night to share what’s believed to be the very first publicly-disclosed instance and proof-of-concept of a kernel exploit for visionOS – the operating system that powers Apple’s Vision Pro.
In the post, Ravichandran shared images of an app they created for Vision Pro that has a button labeled “Crash My Vision Pro” with a skull Emoji wearing a Vision Pro headset on it. When tapped, the Vision Pro crashes. When it comes back up, it does so in full pass-through mode and displays a message for the user that Vision Pro must reboot and that it will go dark after 30 seconds.
Ravichandran also shows off what appears to be the crash log for the kernel panic relating to their kernel exploit. When asked by a follower if Ravichandran was responsible for finding the kernel exploit, he replied with, “Yes, I found it.”

While this is certainly the first time that I’ve seen someone come up with a kernel exploit for Apple’s all-new Vision Pro, it remains to be seen if it’s truly the world’s first. On the other hand, given how short of a time it’s been available to the public, we wouldn’t doubt it.
Kernel exploits are a core component of jailbreaks that allow users to perform actions on a device outside of the parameters set by the company. This includes installing unauthorized software, modifying the aesthetics of the operating system, and unlocking core functionality that Apple locks down with software.
While Ravichandran hasn’t mentioned anything about jailbreaking, or said if they plan to release the kernel exploit publicly, it would be very neat if someone in the jailbreak community could get their hands on a similar kernel exploit and somehow manage to make a jailbreak for Apple’s latest device.
Doing so would likely require a host of other security mitigation-defeating measures, as Apple has systematically beefed-up system security on the hardware and software sides over the past several years to try and thwart jailbreaking. But even today, hackers are still coming up with XTRR bypasses, PPL bypasses, PAC bypasses, and all sorts of other bypasses to get around those.
Are you excited that the Vision Pro is already getting hacked? Let us know your thoughts in the comments section down below.




