The Misaka package manager app for MacDirtyCow and kernel file descriptor (kfd) exploit-vulnerable handsets has received another update on Tuesday, this time bringing the project up to version 8.1.2.
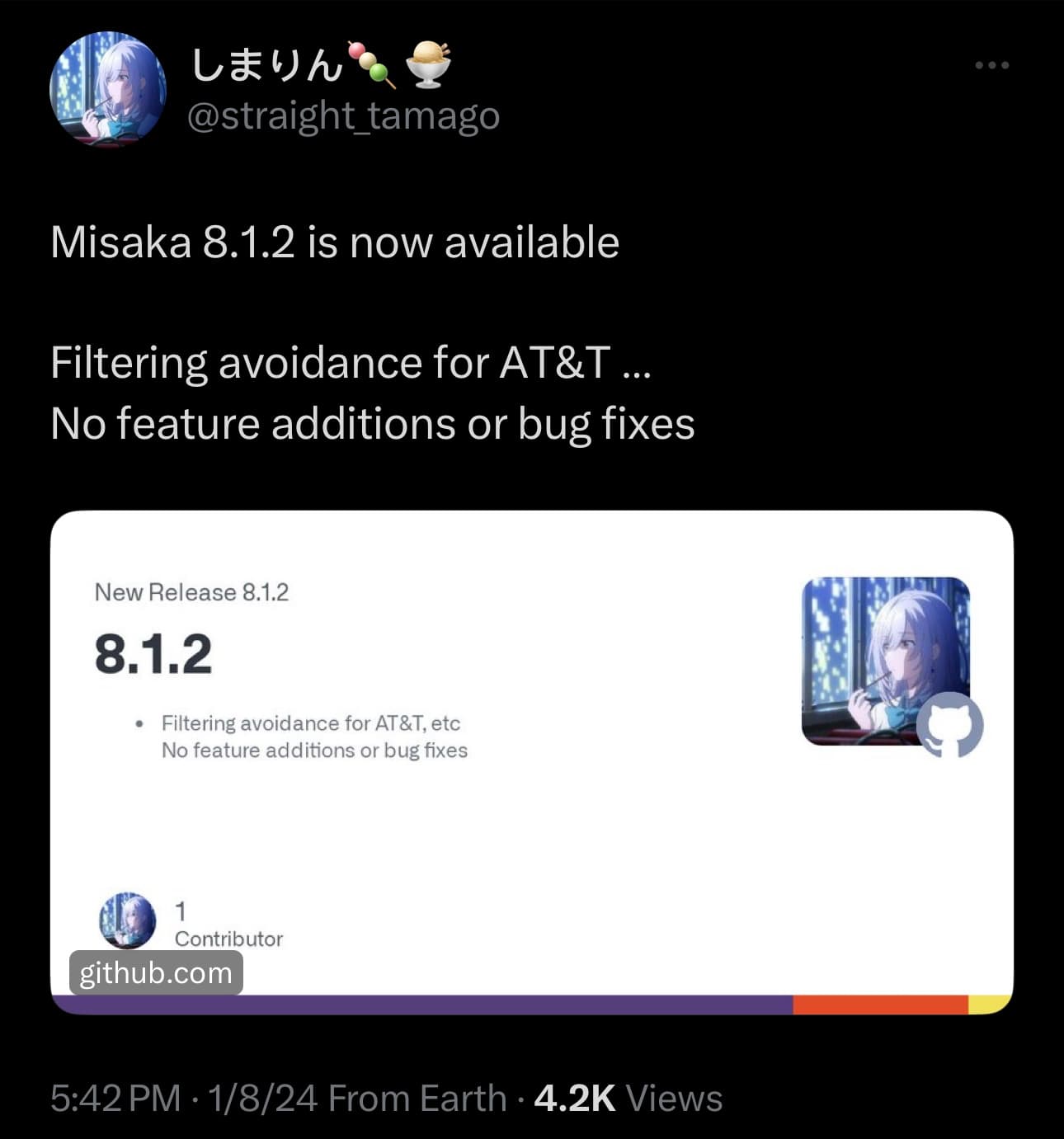
Misaka lead developer @straight_tamago first announced the latest Misaka update via a post shared to X (formerly Twitter), and from what we can gather, this is a relatively minor, yet important update that implements filtering avoidance for the AT&T network.
What do we mean by this exactly? Well according to @straight_tamago, AT&T customers were receiving a nasty message while attempting to use Misaka. As it turns out, AT&T is no friend to iPhone hacks and customizations:
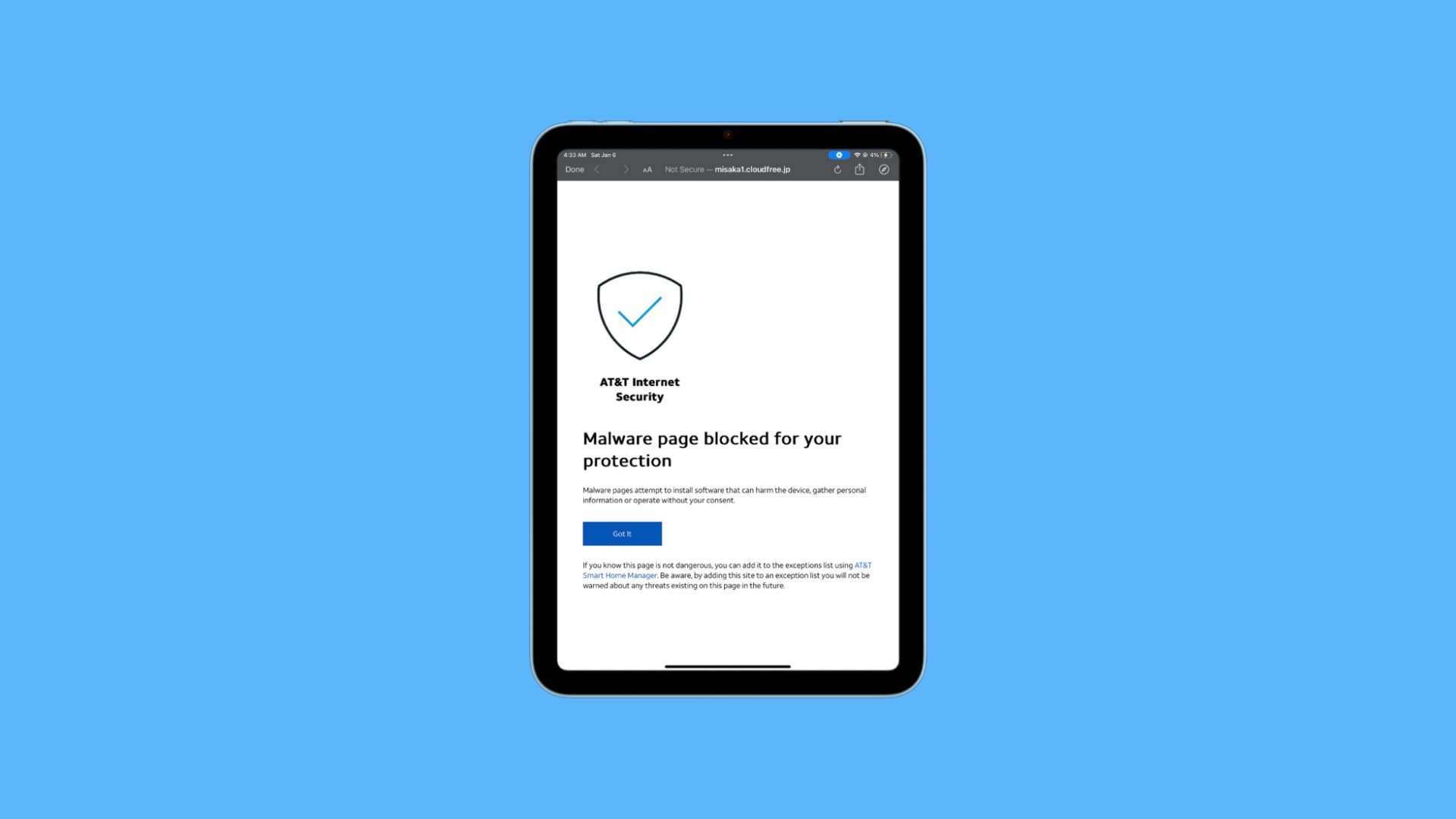
The latest update should prevent Misaka users from seeing the above pop-up so that they can continue using the app as usual.
To be clear, Misaka isn’t the malware AT&T’s pop-up colors it as. But since it’s a hack-based utility, it’s understandable why AT&T’s system might flag it as such. We’ve previously seen similar anti-malware pop-ups affect perfectly safe jailbreak tools as well, so it’s nothing to be alarmed about.
While this update is primarily for AT&T subscribers, all users can install and use it. The latest .ipa is now available via the Misaka project’s GitHub page and can be sideloaded over your existing installation with AltStore or Sideloadly, or perma-signed with TrollStore.
If you’re not already using Misaka, then you can install it using one of the step-by-step tutorials below:
- How to install the Misaka package manager with TrollStore
- How to install the Misaka package manager with Sideloadly
With Misaka, you are able to install hacks and add-ons that exploit the MacDirtyCow bug for iOS & iPadOS 15.0-16.1.2 and the kfd bug for iOS & iPadOS 16.0-16.6.1. Misaka is also a popular installation method for TrollStore 2, and supports JavaScript hacks on iOS & iPadOS 17 as well as tvOS-based hacks via MacDirtyCow.
Are you taking advantage of the latest version of Misaka yet? Be sure to let us know in the comments section down below.




