Just yesterday, we shared how the Misaka package manager app for MacDirtyCow devices would soon pick up support for the newer kernel file descriptor (kfd) exploit for devices running up to and including iOS 16.6 beta 1.
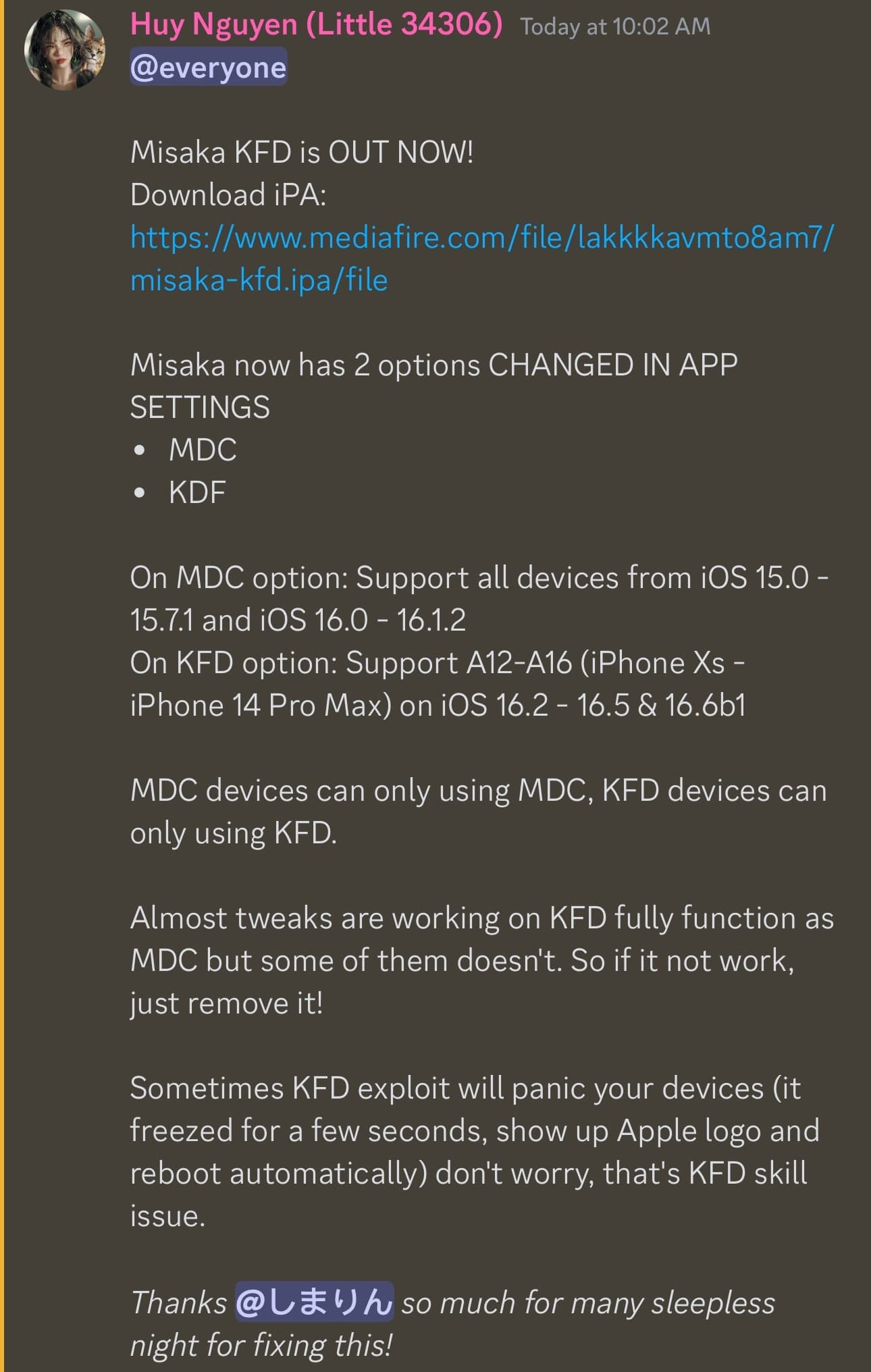
Thursday morning, the Misaka team delivered on that promise with an announcement shared in the Discord server, shown above.
The latest Misaka beta, dubbed version 1.9.3, officially adds support for the new kfd exploit.
According to the announcement, the app comes with two options inside that the user can turn on. One option enables support for the MacDirtyCow exploit on devices running iOS or iPadOS 15.0-16.1.2, while the other enables support for the kfd exploit on A12-A16 devices running iOS or iPadOS 16.2-16.5:
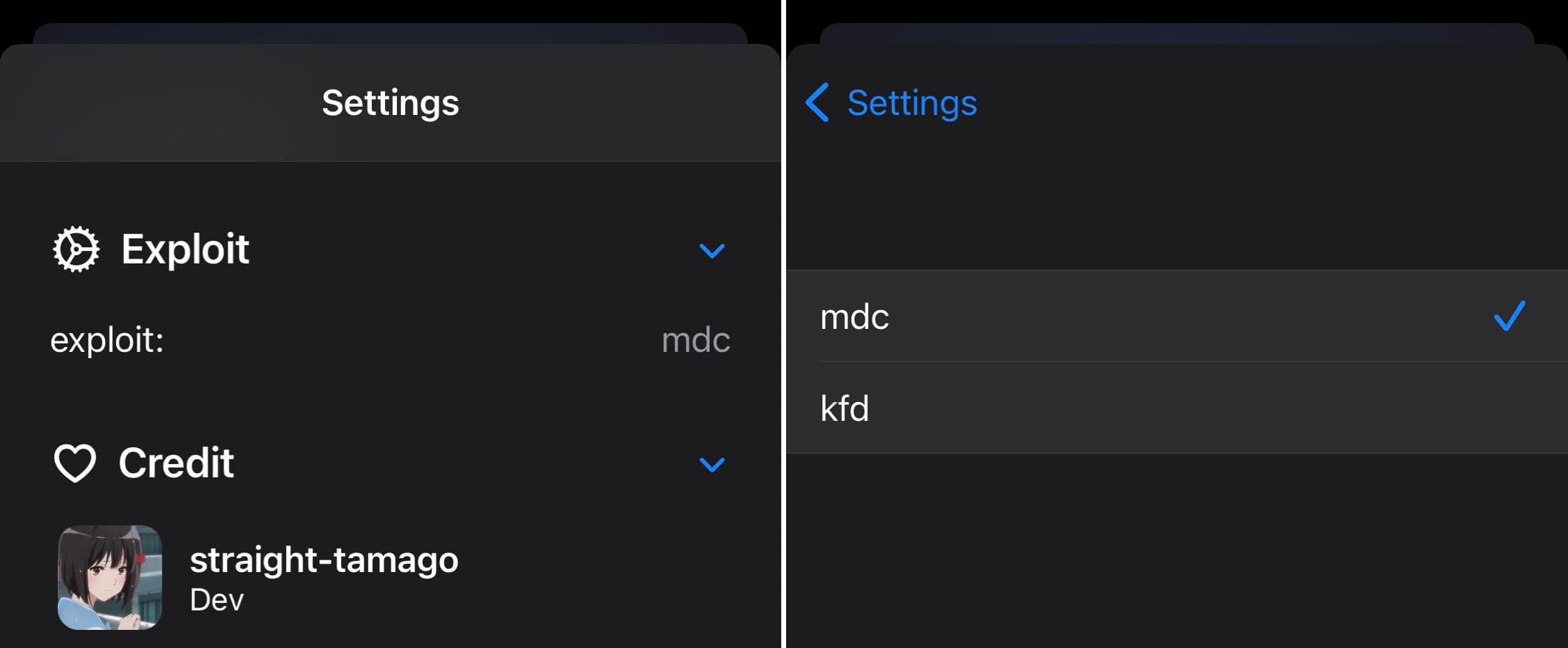
At this time, the Misaka team says that some add-ons designed for use with the MacDirtyCow exploit are already functioning on kfd devices, but not all of them are. Should you come across one that doesn’t work, you can safely remove it without any harm to your device and wait for it to be updated to support kfd.
The team also warns that kfd can sometimes cause unexpected kernel panics. This may be ironed out in the future as developers work out the kinks in kfd, but there’s no telling how long that could take.
If you’re using a kfd device and you’d like to try out Misaka for the first time, then you can follow our step-by-step tutorial to get started.
Are you planning to take advantage of Misaka now that it works on newer firmware? Be sure to let us know in the comments section down below.




