The Misaka package manager app, responsible for providing users with access to numerous repositories that host MacDirtyCow and kfd exploit-supported add-ons, received another update Tuesday evening that might be of interest to some users.
The latest version of Misaka, coined version 2.5.0 beta, was first announced via the project’s dedicated Discord server, as shown above.
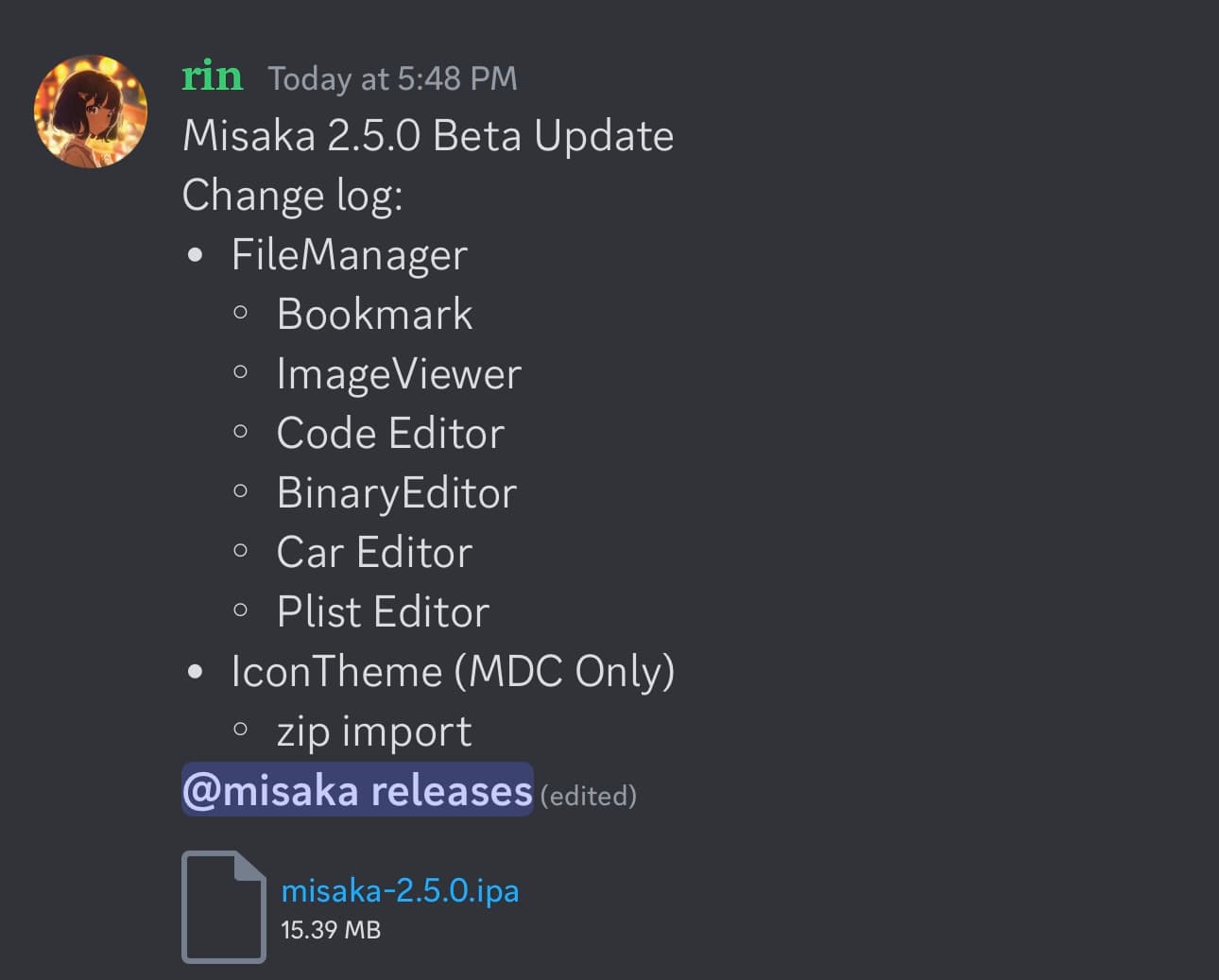
The full change log for the new Misaka v2.5.0 beta update appears to be the following:
– Improvements to the file manager
– Bookmark
– Image Viewer
– Code Editor
– Binary Editor
– Car Editor
– .plist Editor
– Improvements to icon theme (MDC Only)
– .zip import
As you can probably tell, this update puts a lot of its focus on the app’s integrated file manager, which includes the ability to bookmark items, view images, and edit things such as code, binary, .plist files, and more. Of course, the ability to import .zip files for icon theming was another addition in this update.
If you’re already a Misaka package manager app user, then you can download the latest version from the Discord server and simply perma-sign or sideload it to overwrite your existing installation. This will update you to the latest version.
Anyone who isn’t already taking advantage of Misaka, and would like to start today, can head over to our detailed step-by-step walk-through post to learn more about how to install and use the package manager app.
While the Misaka app itself doesn’t require you to have a MacDirtyCow or kfd exploit-vulnerable device, installing and using the add-ons does. The MacDirtyCow exploit covers iOS & iPadOS 15.0-16.1.2, while the kfd exploit covers devices running iOS & iPadOS 16.0-16.6 beta 1.
Are you running the latest version of the Misaka package manager app yet? Be sure to let us know why or why not in the comments section down below.




