At the start of October, Linus Henze took the stage at the Objective by the Sea conference to showcase his Fugu15 jailbreak on an iPhone running iOS 15.4.1 with a slick new installation method that reminded a lot of us of the JailbreakMe days. And as of this Monday, it’s officially released and open source on Henze’s GitHub page.
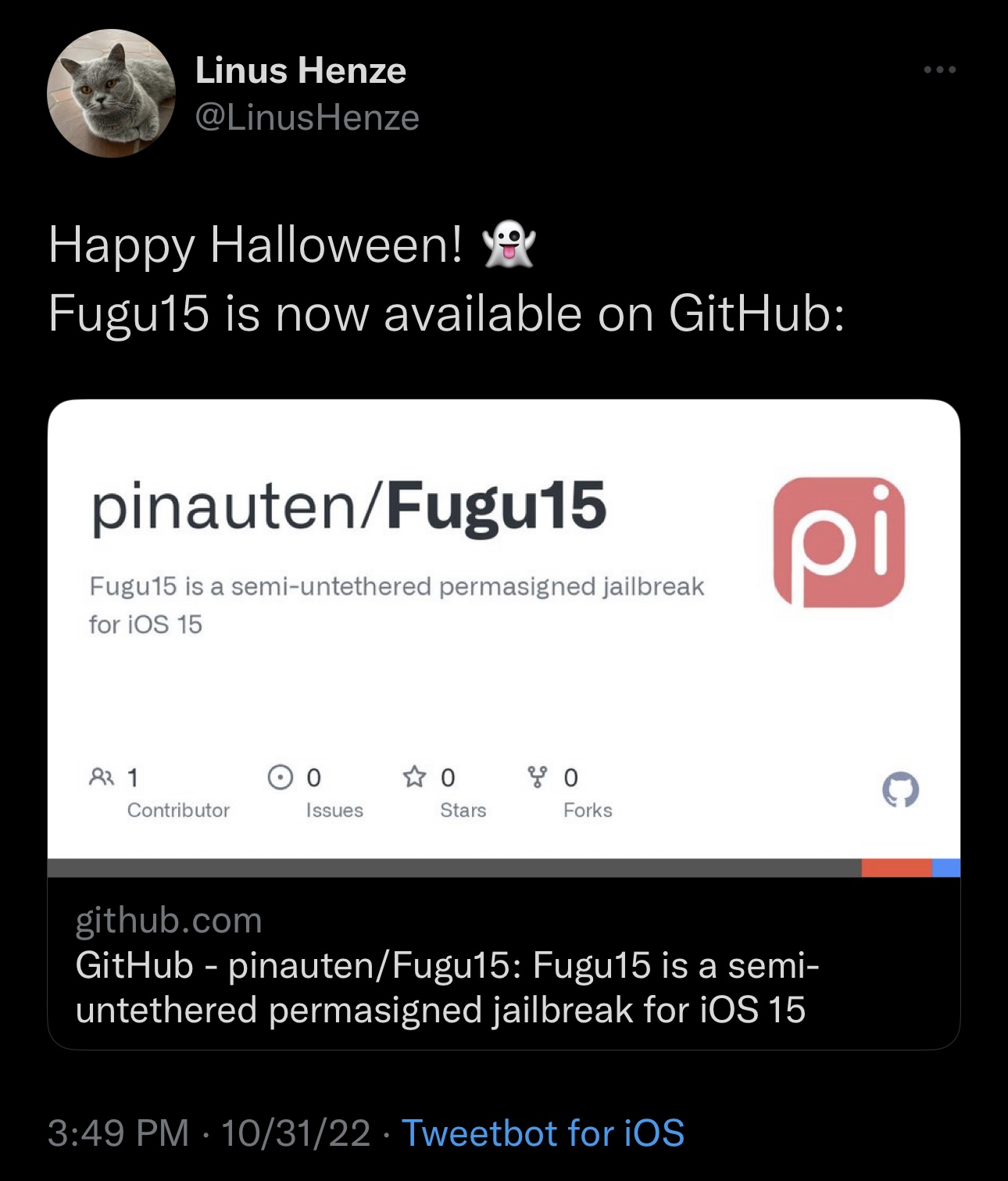
Henze announced the Fugu15 release via Twitter this afternoon, but before getting too excited, we should mention right off the bay that Fugu15 is a jailbreak primarily intended for developers as there aren’t currently any iOS or iPadOS 15-supported jailbreak tweaks right now due to the lack of a tweak injection library (the same issue currently delays the Odyssey Team’s Cheyote jailbreak).
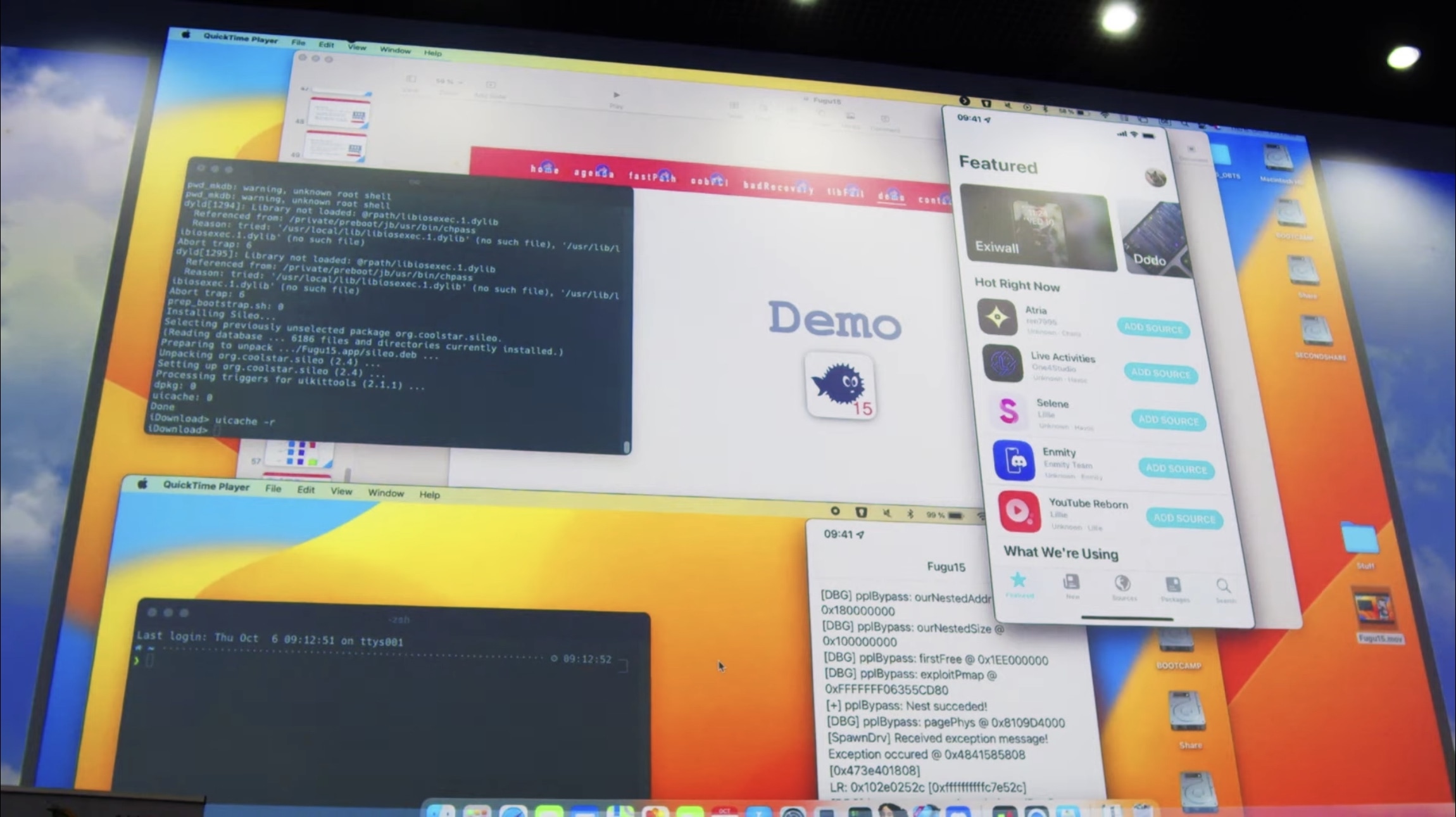
What is Fugu15?
Fugu15 is a semi-untethered and perma-signed jailbreak app that supports certain arm64e devices running iOS & iPadOS 15.0-15.4.1, and it runs the Procursus bootstrap with the Sileo package manager. Because it’s semi-untethered, a computer isn’t needed to re-jailbreak, but you will need to re-jailbreak every time you reboot your device. Moreover, a CoreTrust bug allows Fugu15 to remain signed indefinitely, so it doesn’t need to be re-signed every seven days.
If this sounds familiar, then that’s because TrollStore uses the same CoreTrust bug. TrollStore allows users to sideload and perma-sign any .ipa file on their device.
The Fugu15 release includes a code-signing bypass, a kernel exploit, a kernel PAC bypass, and a PPL bypass. It’s worth noting that Fugu15 can be installed either via Safari if you own a domain, or with a USB connection and Xcode on a Mac.
What you need to know about Fugu15
But as we noted earlier, Fugu15 is a developer-oriented jailbreak, so it’s not really all that useful for the average Joe. That’s because there are currently no compatible jailbreak tweaks and because it’s buggy on certain early firmware versions and isn’t thoroughly tested on all devices.
In fact, Henze notes on the GitHub page that Fugu15 has only been extensively tested on the following device setups:
- iPhone XS Max running iOS 15.4.1
- iPhone 11 (Security Research Device) running iOS 15.4.1
- iPhone 12 (Security Research Device) running iOS 15.4.1
- iPhone 12 Pro Max running iOS 15.4.1
- iPhone 13 offline edition running iOS 15.1
Fugu15 may be compatible with other device and firmware combinations, however it hasn’t been extensively tested on them. At this time, only arm64e devices are supported (iPhone XS and newer, or devices with the A12 chip or newer).
So far, Henze is aware of the following bugs, but there may be others:
1) If oobPCI (the process exploiting the kernel) exits, the system might be left in an inconsistent state and panic at some point. This usually occurs about 5 seconds after running the
exit_fullcommand in iDownload.
Workaround: Don’t quit oobPCI or make sure to do it as fast as possible to reduce the chance of a kernel panic. The reason for this panic is currently unknown.
2) When not connected to power, entering deep sleep will cause a kernel panic due to a bug in DriverKit (also happened with Fugu14). Unfortunately, the fix from Fugu14 does not work on iOS 15.
Workaround: This bug will not occur when quitting oobPCI. However, the bug described above may occur when oobPCI exits.
3) Some iOS versions (at least iOS 15.1 and below, maybe 15.2 and 15.3 too) have a DriverKit bug which causes bus mastering to be disabled for the WiFi chip when running oobPCI, causing a kernel panic when WiFi is used. This bug can be fixed but a fix is not included in Fugu15 at the moment.
Workaround: Disable WiFi.
A brief F.A.Q. from Linus Henze regarding Fugu15
In a section entitled F.A.Q. on the GitHub page, Henze answers some pertinent questions that we’ll outline below:
Q: I’m an end user. Is Fugu15 useful to me?
A: No.
Q: My iOS version/device is not supported by Fugu15, will you add support for it?
A: No. (I’m done with iOS 15)
Q: Will you ever add support for tweak injection?
A: No.
Q: Do you provide official support for Fugu15? Are any updates planned?
A: No.
Q: I installed/updated something through Sileo but it won’t launch. How can I fix that?
A: Fugu15 uses TrustCache injection to bypass code signing. Therefore, if you install or update something, it’s code signature must be in a TrustCache. You can load additional TrustCaches from the iDownload shell via the tcload command.
Q: Wen eta Fugu16??????
A: …
What will become of Fugu15?
Obviously, Henze has no intention of developing Fugu15 any further since he’s shifting his attention away from iOS & iPadOS 15, and likely toward iOS & iPadOS 16 going forward. On the other hand, releasing and open-sourcing Fugu15 could prove useful to the jailbreak community as it may lend assistance to struggling jailbreak developers who need more ideas for attacking iOS & iPadOS 15 for those who’ve been patiently waiting for so long.
That said, while it’s a useful jailbreak for developers who need to test stuff, it’s mostly a proof of concept in its current stages.
Conclusion
While the release of Fugu15 is indeed good news and highly anticipated, the Fugu15 project itself isn’t a jailbreak that anybody should be rushing to download and install. Instead, users should stay on the lowest possible firmware and wait for a public-friendly iOS & iPadOS 15 jailbreak with working tweak injection – since that’s what most of us jailbreak for anyway.
You can learn more about Fugu15 and what it’s all about by visiting Linus Henze’s GitHub page.
Are you excited that Fugu15 has finally been released? Be sure to discuss your thoughts about it in the comments section down below.




