Jailbreak tweaks are generally installed on iPhones and iPads that have been jailbroken, but the community has been hard at work on utilities that allow tweak injection to exist on non-jailbroken devices by way of kernel exploits such as kernel file descriptor (kfd) and the new CoreTrust bug utilized by TrollStore 2.
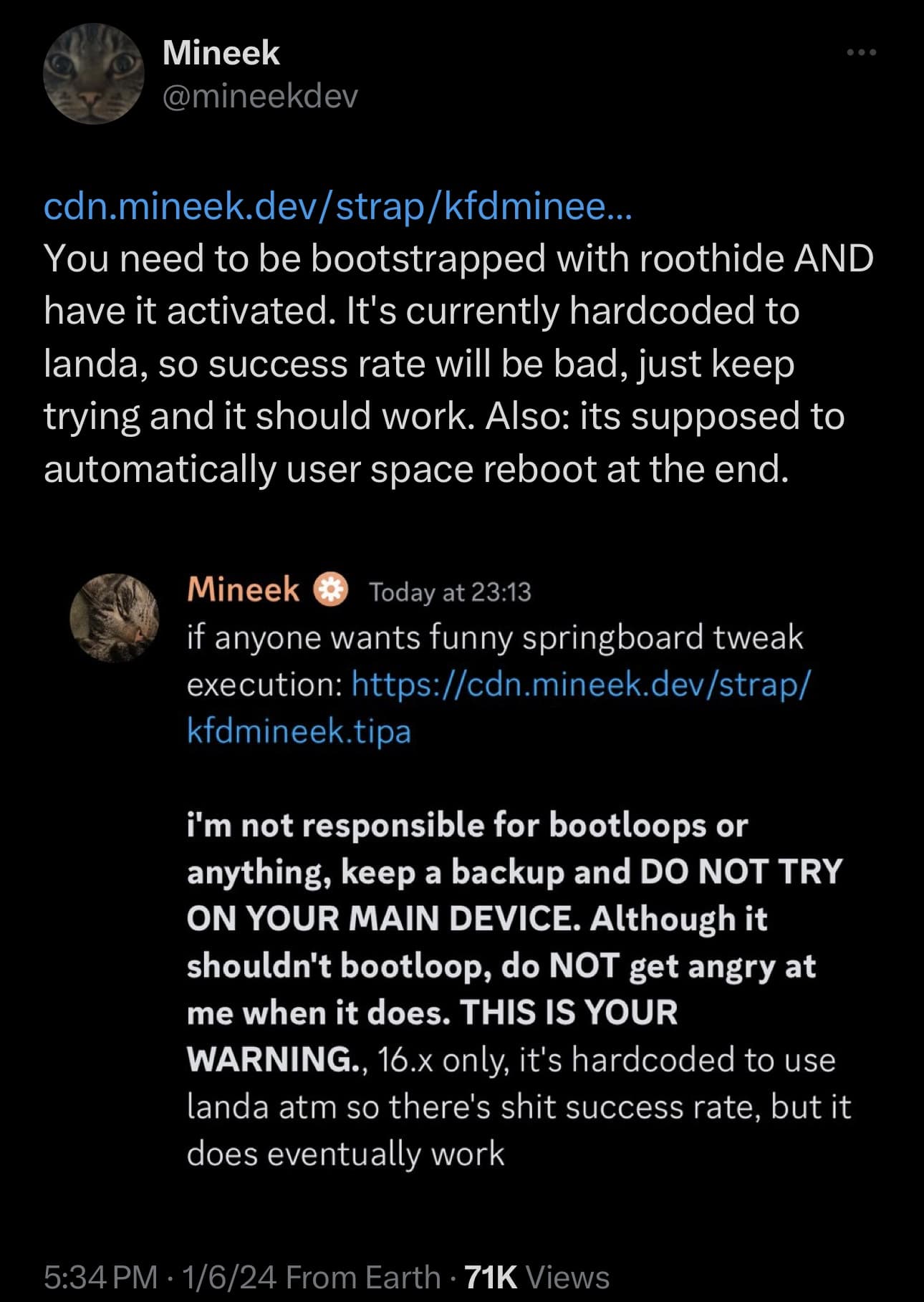
Just this weekend, iOS developer @mineekdev took to X (formerly Twitter) to share what appears to be a working tweak injection method for iOS & iPadOS 16 devices vulnerable to the kfd exploit that can be installed using the TrollStore perma-signing utility.
The project, dubbed kfdmineek, is available via a dedicated GitHub page and is described as “tweak injection on arm64e iOS 16 versions.” In other words, you can use this project alongside the RootHide development team’s Procursus bootstrap to install and load certain jailbreak tweaks even if you aren’t jailbroken and all you have is TrollStore 2.
There is a particularly giant asterisk though, and you should be vividly familiar with it before you consider giving this a try. There’s a very real possibility of boot-looping your device, and for that reason, most users should avoid using this (and even advanced users should avoid using this on their main device).
Project lead developer @mineekdev echoed this warning when announcing it via their Discord server:
The warning below:
I am not responsible for boot-loops or anything. Keep a backup and do not try this on your main device. Although it shouldn’t boot-loop, do not get angry at me when it does. This is your warning.
The warning may sound particularly familiar to that of jailbreaking. If you remember, there was always a “try this at your own risk” attached to jailbreak tools a long time ago, and while we see a lot less of that today, there’s always an inherent risk to device stability when it comes to hacking.
In this particular case, however, the code isn’t particularly clean and even @mineekdev admits this on the GitHub page. That said, there is a higher risk of things going wrong using something like this than with a traditional jailbreak, and there’s also a poor success rate because it utilizes kfd and puaf_landa. These factors may turn ordinary users away, and given the nature of it, that’s probably a good thing.
In any case, it’s still really neat to see developers making things like this because it demonstrates what may be possible with the tools we have at our disposal currently.
Also see: ElleKit developer says tweak injection for iOS 17.0 almost ready
It may be possible for some of these hacks and methods to be made safer in the future as the projects evolve, so users should probably just sit tight to see what happens instead of using it themselves, or better yet, wait for the iOS & iPadOS 16.0-16.5.1 jailbreak that should be possible on arm64e devices when Kaspersky publishes a writeup on their PPL bypass.
What are your thoughts on running tweak injection without a jailbreak? Discuss in the comments section down below.




